Introduction
The Domain Name System (DNS) is a critical component of the internet infrastructure. DNS is responsible for resolving hostnames into IP addresses. If DNS fails, online applications, services, and third-party web APIs that many applications depend on, will become unavailable. DNS service is increasingly becoming a prime target for Distributed Denial of Service (DDoS) attacks.
DNS DDoS attacks can cause significant disruptions to internet services, resulting in service unavailability, slow response times, and even complete network outages. These attacks can also lead to significant financial losses and damage to a company’s reputation.
As attackers become more sophisticated, the risks associated with DNS DDoS attacks continue to grow. In recent years, we have seen an increase in the scale and frequency of DNS DDoS attacks, and attackers are constantly innovating new techniques to evade detection and cause maximum damage.
Understanding DNS Open Resolvers
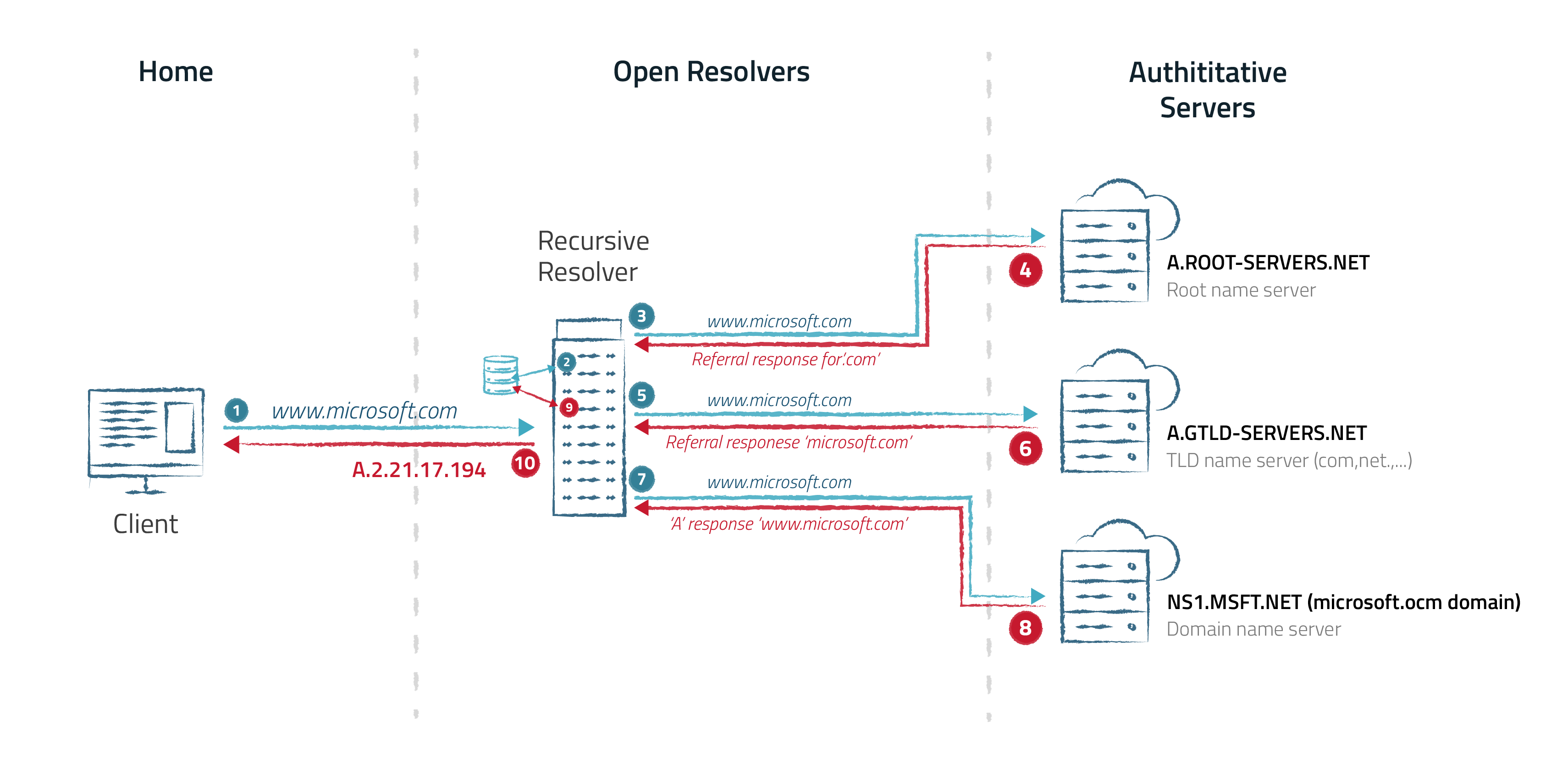
The Domain Name System (DNS) is akin to the internet's address book, translating human-readable domain names into machine-readable IP addresses. This translation process is vital for accessing websites, sending emails, and performing various online activities. At the heart of this system are DNS resolvers, which facilitate the resolution of domain names to IP addresses.
DNS resolvers come in various forms, including authoritative DNS servers, recursive resolvers, and open resolvers. While authoritative DNS servers are responsible for hosting and providing authoritative answers for specific domain zones, recursive resolvers play a crucial role in navigating the DNS hierarchy to resolve queries by recursively querying other DNS servers until they obtain the final answer.
Open resolvers, however, serve a unique function in the DNS ecosystem. Unlike authoritative and recursive resolvers, open resolvers accept and respond to DNS queries from any source, regardless of whether they are within the resolver's administrative domain. Open resolvers operate as public DNS servers, providing resolution services to any requester on the internet.
What is DNS Open Resolver?
Some DNS servers perform their hierarchical lookups by means of recursion, and rather than limit the ability to make recursive requests to local or authorized clients, DNS servers referred to as Open Resolvers allow recursive DNS requests from any client.
Key Characteristics of DNS Open Resolvers
Accessibility: Open resolvers are publicly accessible, meaning they accept DNS queries from any source without authentication or authorization requirements. This accessibility makes it convenient for users seeking to resolve domain names without relying on their ISP's DNS servers or other private resolvers.
Recursion: Similar to recursive resolvers, open resolvers perform recursive resolution by querying authoritative DNS servers on behalf of requesters to obtain the final answer to a DNS query. This recursive behavior enables them to navigate the DNS hierarchy and resolve queries for any domain name.
Decentralization: Open resolvers are distributed across the internet, operated by various entities, including ISPs, universities, public DNS service providers, and organizations. This decentralization contributes to the resilience and redundancy of the DNS infrastructure but also complicates efforts to secure and monitor open resolver operations effectively.
Risks of DNS Open Resolvers
Potential for Abuse: While open resolvers offer convenience and accessibility, they also pose inherent security risks. Attackers can exploit open resolvers to amplify and reflect DNS traffic as part of DDoS attacks, manipulate DNS responses to redirect users to malicious websites, or conduct reconnaissance activities to gather information about target networks.
Amplification and Reflection Attacks: The unrestricted accessibility of open resolvers makes them susceptible to exploitation in DNS amplification and reflection attacks. Attackers leverage open resolvers to amplify DNS traffic directed at a target by sending spoofed queries, leading to volumetric DDoS attacks with magnified impact.
DNS Authoritative Perspective: Managing and securing DNS authoritative infrastructure becomes challenging when it must be open to open resolvers, that may be misconfigured, unpatched or abused to launch reflection amplification DNS DDoS attacks.
Misconfiguration and Unpatched Resolvers: Open resolvers may be misconfigured or lack important DNS updates that leave them susceptible to security threats.
Security Challenges
With the DNS infrastructure comprised of open resolvers, among other ISP resolvers, the attackers and legitimate users send their queries over the same infrastructure. In that sense, open resolvers act like 'proxies' and redirect DNS queries for both attackers and legitimate clients. As such, open resolvers comprise a legitimate source of queries towards the DNS authoritative servers, that cannot be blocked. This imposes a challenge for accurate detection and mitigation from the DNS authoritative perspective.
In addition, the adoption of RFC 5452 by DNS resolvers creates new challenges for authoritative DNS security. According to RFC 5452, a DNS resolver must apply certain security measures to protect itself from DNS cache poisoning threats. These measures include dynamic alternation of DNS and IP headers upon every new DNS query. Some DNS resolvers even alter their source IP between queries.
Security challenge #1
– How to identify and deny only bad queries from a legitimate open resolver?
Security challenge #2
– How to identify misbehaving open resolvers that are compromised by attackers for reflection and amplification?
Security challenge #3
– How to identify and validate good open resolvers when they dynamically alter their source IP?
The challenge for authoritative DNS protection is twofold; authoritative servers must allow queries from open resolvers even though they may be compromised and used by attackers, and second from authoritative perspective there is a need to authenticate legitimate resolvers, and RFC 5452 makes it even more challenging.
Security Strategies
Given the above challenges and risks, here are a few recommended strategies for securing authoritative DNS servers:
Strategy for Security Challenge #1 – Behavioral AI-based Security is imperative to identify attack DNS traffic and isolate it, without impact on legitimate traffic. Behavioral AI-based analysis combined with Positive Security Model ensures that your DNS protection can distinguish between good and bad queries, even when originating from legitimate resolvers. For optimal seamless security, it is best that the security system automatically learns the good DNS queries without any network pre-requisites or pre-loaded lists.
Strategy for Security Challenge #2 – Resolver Behavior Analysis is critical to identify scenarios when legitimate resolvers become compromised and exploited for attacks. Especially with DNS, where legitimate and attack traffic can originate from the same open resolvers. Security solutions that rely on source-blocking impose false positive risks. A preferred strategy would be surgical mitigation according to the resolver's behavior.
Strategy for Security Challenge #3 – Smart Authentication of DNS resolvers is required as more resolvers comply with RFC 5452. Traditional DNS challenge-response that does not consider RFC 5452 will become ineffective. The preferred approach is a DNS challenge-response that is fully compliant with DNS protocol and agnostic to L3 characteristics.
Summary
DNS open resolvers play a significant role in facilitating DNS resolution on the internet, offering accessibility and convenience to users worldwide. However, their open nature also introduces security risks and operational challenges, necessitating proactive measures to secure and monitor open resolver operations effectively.
Organizations requiring DNS protection must reevaluate their security measures. Traditional DNS solutions may seize to be effective considering DNS attacks vectors, the wide usage of DNS open resolver and DNS compliance adoption.
Security admins need to boost up DNS security with AI-powered technology that can win all the challenges and achieve automatic detection and mitigation of DNS attacks, without human intervention. This is the only way to ensure fastest Time to Mitigation (TTM) and continuous DNS service even while under attack.