
Carding is an automated form of payment fraud in which fraudsters test a bulk list of credit or debit card data against a merchant’s payment processing system to verify breached or stolen card details. Such card details are stolen from different payment channels, taken from another application, or purchased from dark web marketplaces. Both carding and card cracking are acknowledged by the Open Worldwide Application Security Project® (OWASP) as methods of obtaining card details.
In this widely prevalent form of financial fraud, attackers leverage the power of sophisticated bots to carry out credential stuffing and credential cracking attacks to identify valid accounts which can be targeted for fraud, cashed out or used to make unauthorized purchases. Valid bank and credit card details can also be illegally obtained through either malware installed on targeted devices or phishing and social engineering tactics that trick victims into unwittingly revealing their card and/or other personal information.
Between 2023 and 2027, carding is expected to result in cumulative global merchant losses to online payment fraud exceeding $343 billion, according to Juniper Research.
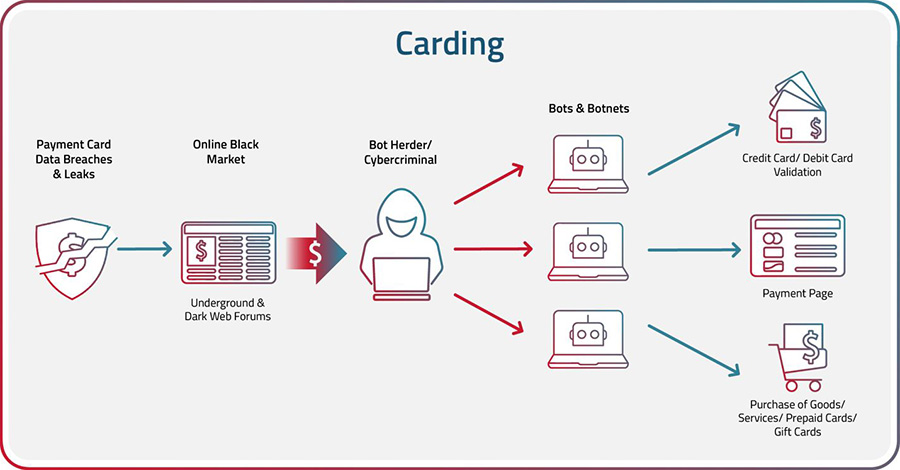
The process of executing a carding attack typically involves several steps:
- Obtain Credit/Debit Card Information: Carders obtain credit card information by stealing physical credit cards, purchasing credit card data on the dark web, or using techniques such as phishing, skimming, or malware to steal credit card information. Account Takeover (ATO) of user accounts on e-commerce or financial websites carried out by bots is yet another way for bad actors to steal payment card data.
- Validate Card Data: After carders obtain payment card data, they often use bots to validate the cards and check the balances or credit limits on the card with credential stuffing and credential cracking. Credential stuffing is a technique that uses bots to rapidly enter lists of breached or stolen card data to try to validate them. Credential cracking is the process of entering random characters over multiple attempts in the hope of eventually guessing the right combination.
- Drop Shipping: A drop is a location where the fraudster can have fraudulently purchased items shipped without revealing their own identity or location.
- Make the Purchase: The cybercriminal can use the stolen credit card information to make purchases online or in-store. They may use a technique known as "card present" fraud to create a counterfeit card and make purchases in-person. "Card not present" fraud indicates when the purchase was made online.
- Keep or Resell the Goods: Once fraudsters receive the fraudulently purchased items, they will either keep them for personal use or resell them on the black market for cash.
Infographic: The Stages of Carding:
Phishing: Cybercriminals send a fake email or text message to the victim, posing as a legitimate company. They request that the victim provides their credit/debit card information, which they can use to make fraudulent purchases.
Social Engineering: The fraudster poses as a legitimate representative of a company or financial institution and convinces the victim to provide their credit card information over the phone or through email.
Identity Theft: A thief steals a victim's personal information, such as their name, address and social security number, and uses that information to open new credit card accounts or make purchases using the victim's existing credit card.
Malware: Nefarious actors install malicious software on a computer or mobile device to capture the victim's payment card information when they make online purchases.
Card Skimming: In this type of fraud, criminals use a device known as a skimmer to steal credit card information. The skimmer is placed on a legitimate card reader, such as an ATM or gas pump, and records the card data when the victim swipes or inserts their card.
Basic Carding Attack Prevention Measures:
Anomalous Activity Monitoring: Organizations that handle payment cards should look out for anomalies in billing or shipping information and buying patterns. They should also track account holders’ IP addresses and/or location to detect carding fraud. Also recommended is real-time monitoring, especially when a customer makes multiple rapid purchases. This could point to automated validation activities of breached or stolen card data, as well as solutions that verify if a card has been reported as stolen or used to commit fraud.
Banking Industry Measures: PCI-DSS (Payment Card Industry Data Security Standard) and Mastercard’s Identity Check are key examples of measures that aim to reduce carding fraud by promoting and enforcing data security standards. They leverage several types of identifying data to ensure that only cardholders, not bots, are able to carry out online transactions.
OWASP Countermeasures: The Open Web Application Security Project (OWASP), a non-profit organization focused on improving the security of software, suggests a list of countermeasures to address carding attacks, such as:
- Outsourcing all aspects of payments to providers with adequate facilities to address carding attacks
- Increasing the minimum checkout value
- IP blacklisting of known bot and cyber-fraud origins
Sophisticated Carding Attack Prevention:
Carding and payment fraud are constantly evolving to evade basic countermeasures, and fraudulent tactics that trick cardholders through phishing and social engineering techniques can still be successfully executed before the cardholder or payment processor can detect the fraud. More stringent measures against automated carding attacks are required to prevent them before they can carry out fraud or other types of bot attacks.
Responding to these potential threats, many organizations that regularly face bot attacks have implemented specialized, dedicated bot mitigation solutions such as Radware Bot Manager. Bot Manager goes far beyond basic prevention measures and combines multiple approaches for bot detection. Techniques include deep user behavior and intent analysis, semi-supervised machine learning algorithms, collective bot intelligence, and fingerprinting to effectively eliminate carding attacks before they happen.