The Lazarus Group, also known as APT38, is a notorious Advanced Persistent Threat (APT) entity believed to be linked to North Korean hackers. They have made a significant impact on global cybersecurity, conducting high-profile financial cyberattacks and engaging in cyber espionage. Their operations often involve the deployment of sophisticated malware, the analysis of which provides valuable threat intelligence for the cybersecurity community.
The group's activities are aligned with North Korea's political interests, and they have targeted various countries including South Korea, the U.S., and many others. Their tactics include spear-phishing, watering hole attacks, and exploiting zero-day vulnerabilities. They have also been known to disable monitoring protocols in victims’ operating systems to evade detection. Despite their efforts to remain hidden, their activities have been extensively documented through malware analysis and threat intelligence, contributing to our understanding of their methods and objectives.
The Lazarus Group, also known as APT38, is a cyber espionage group that has been active since at least 2009. This group is believed to be based in North Korea and is associated with the North Korean government's Reconnaissance General Bureau. The group has targeted banks, financial institutions, casinos, cryptocurrency exchanges, SWIFT system endpoints, and ATMs in at least 38 countries worldwide with sophisticated cross-platform attacks.
The United States Federal Bureau of Investigation says that the Lazarus Group is allegedly a North Korean “state-sponsored hacking organization”. According to North Korean defector Kim Kuk-song, the unit is internally known in North Korea as 414 Liaison Office.
The History of Lazarus Group
The Lazarus Group has evolved over the years with a significant escalation in the sophistication of their tactics and the scale of their operations.
One of the earliest known attacks attributed to the Lazarus Group is “Operation Troy”, which took place from 2009 to 2012. This was a cyber-espionage campaign that utilized unsophisticated distributed denial-of-service attack (DDoS) techniques to target the South Korean government in Seoul.
The group's operations took a significant leap in sophistication with the 2014 attack on Sony Pictures. This attack involved more advanced techniques and highlighted how much the group had evolved over time. The Lazarus Group were reported to have stolen US$12 million from the Banco del Austro in Ecuador and US$1 million from Vietnam's Tien Phong Bank in 2015. They have also targeted banks in Poland and Mexico.
The group's activities escalated further with the 2016 bank heist, which included an attack on the Bangladesh Bank, successfully stealing US$81 million. In 2017, the Lazarus group was reported to have stolen US$60 million from the Far Eastern International Bank of Taiwan although the actual amount stolen was unclear, and most of the funds were recovered.
These high-profile attacks brought the Lazarus Group into prominence and established them as a significant threat in the realm of cybersecurity.
The Lazarus Group is known for its adaptability and the breadth of its toolkit. They continuously evolve their tactics and tools, making them a significant cybersecurity threat that leverages techniques such as:
Zero-days: Lazarus Group has been observed exploiting zero-day vulnerabilities in software to breach targets. For instance, they exploited a zero-day vulnerability in a popular certificate software to compromise a South Korean financial entity twice within a span of a year. They also leveraged an ActiveX zero-day vulnerability to attack a South Korean think tank.
Spear Phishing: The group often uses spear phishing techniques, where they send targeted emails to individuals within organizations. These emails typically contain malicious links or attachments. For instance, they have used LinkedIn to trick targets into installing malicious files such as Word documents with hidden macros.
Disinformation: While specific instances of disinformation campaigns by the Lazarus Group are not readily available, they have been known to use misdirection techniques in their campaigns. Some operations were disguised as hacktivist activities, with groups such as “GOP,” “WhoAmI,” and “New Romanic Army” claiming responsibility for these alleged hacktivism attacks.
Malware: Lazarus Group uses a range of custom-built malware, such as remote access trojans (RATs), backdoors, and botnets. They have used the RATANKBA malware to target cryptocurrency companies. They also deployed the Manuscrypt backdoor via macro-laced documents in phishing attacks.
Backdoors: The group uses backdoors to maintain access to compromised systems. For instance, they used the Manuscrypt (aka NukeSped) backdoor in their phishing attacks. They also deployed the BLINDINGCAN and COPPERHEDGE implants in their attacks against the defense industry.
Droppers: The Lazarus Group has been known to use droppers, which are typically used in cyberattacks to install malware onto a target system.
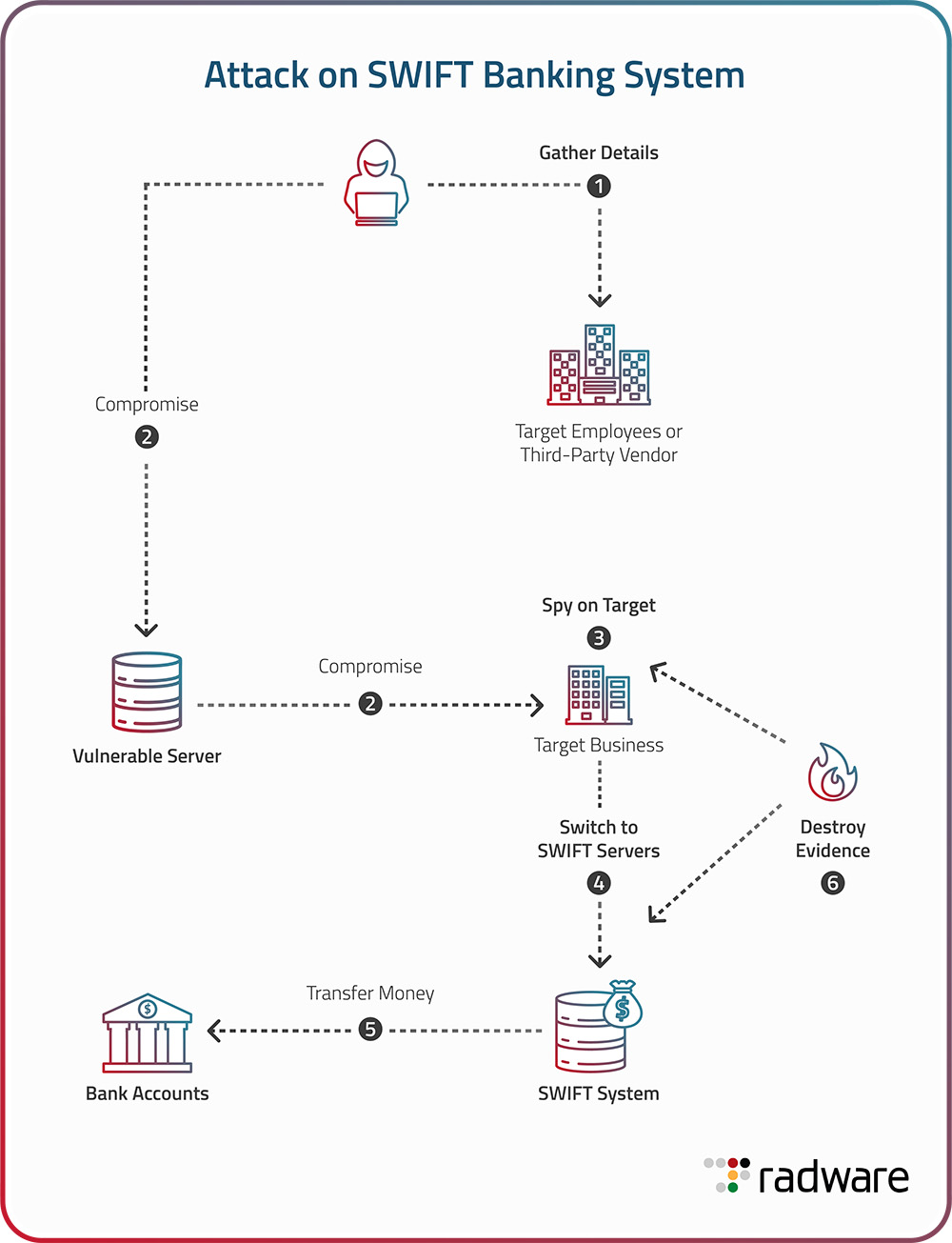
Figure 1: Technique used in SWIFT banking system attack
Some of the biggest cyberattacks carried out by Lazarus Group are:
Sony Pictures Hack (2014): The attack on Sony Pictures Entertainment had far-reaching consequences, resulting in the leak of unreleased films, scripts, and a trove of sensitive personal and corporate data. The attack caused significant reputational damage to Sony and led to the cancellation of the theatrical release of “The Interview,” a comedy film that was a focal point of the hack.
Operation Troy (2009-2012): This was a cyber-espionage campaign that utilized unsophisticated distributed denial-of-service attack (DDoS) techniques to target the South Korean government in Seoul. The attacks were disruptive and marked the beginning of Lazarus Group's operations.
Bangladesh Bank Heist (2016): The attempted theft of $1 billion from Bangladesh's central bank was one of the largest bank heists in history. Although most of the transactions were halted, the group successfully transferred $81 million to accounts in the Philippines. The heist exposed significant vulnerabilities in the SWIFT banking system and led to calls for improved security measures. As of 2018, only around $18 million of the $81 million transferred to the Philippines has been recovered.
WannaCry Ransomware Attack (2017): The WannaCry ransomware attack had a global impact, affecting hundreds of thousands of computers in over 150 countries. The attack caused significant disruption, particularly in the healthcare sector where hospitals in the UK were forced to divert emergency patients. The attack highlighted the dangers of nation-state cyber activities and led to increased focus on cybersecurity in critical infrastructure.
Supply Chain Attacks (2023): The recent campaign targeting organizations worldwide by exploiting legitimate software has shown the group's continued evolution and adaptability. This campaign has raised concerns about supply chain security and has led to increased focus on securing software development processes.
Cryptocurrency Attacks (2018-Present): The Lazarus Group's attacks on cryptocurrency companies have resulted in significant financial losses. These attacks have also highlighted the vulnerabilities inherent in cryptocurrency systems and have led to calls for improved security measures in the cryptocurrency sector.
These attacks have not only caused significant financial and operational damage but have also led to increased awareness and focus on cybersecurity across various sectors.
Radware provides a comprehensive approach to protect against threats posed by sophisticated actors like the Lazarus Group (APT38):
DDoS Protection: Radware is a proven a leader in , a common tactic employed by APT38. Radware's solutions can identify and mitigate such attacks, protecting organizations from potential service disruptions and data breaches.
Threat Intelligence: Radware's threat intelligence capabilities allow it to identify and respond to threats from actors like APT38 to protect customers from DDoS attacks, ransomware attacks, and other threats.
Asset Protection: Radware focuses on protecting critical digital assets across all sizes of companies in all industries. This is particularly relevant given APT38's focus on financial institutions, banks, casinos, cryptocurrency exchanges, SWIFT system endpoints, and ATMs.
Ransom Mitigation: Radware helps organizations avoid paying ransoms by providing robust security measures that prevent attacks by malicious actors like the Lazarus Group from succeeding.
Persistent Threat Monitoring: Radware considers ransom DDoS as a persistent threat and an integral part of the DDoS threat landscape, and continually monitors threat actors such as the Lazarus Group and their attacks to protect Radware customers.
Radware's comprehensive protection strategy involves multiple layers of defense to ensure robust security against sophisticated actors like APT38. By combining advanced DDoS protection, threat intelligence, asset protection, ransom mitigation, and persistent threat monitoring, Radware provides a formidable defense against the specific threats introduced by groups like APT38.