As the 2018 Winter Olympics approaches, Radware ERT Threat Research team turns its attention to the crowds and the target rich environments created by high profile sporting events.
Download a Copy Now
Abstract
As the 2018 Winter Olympics approaches, Radware ERT Threat Research team turns its attention to the crowds and the target rich environments created by high profile sporting events. With over one million tickets for sale, this event will bring large crowds that will demand connectivity and are expected to consume record-breaking volumes. This enormous demand for connectivity and technology will also pose a security risk for Olympic organizers, partners, sponsors, suppliers, service providers and attendees.
Over the last decade there have been a number of cybersecurity related events aimed at the Olympics, like in London 2012i and Rio 2016ii. The potential risk steadily increases as future games become even more connected. 2018 Winter Olympics have the potential to be one of the more vulnerable sporting events in modern history and will provide cyber criminals with numerous opportunities.
This alert will outline risks and precautions for attendees, athletes and sponsors to take before and during the 2018 Olympics in PyeongChang.
Background
There are only a few sporting events in the world as large as the Olympics. With millions of global viewers the Olympics generate a lot of excitement and demand from the fans. Beyond just the games itself the variety of multimedia technologies available for streaming content, augmented reality, IoT, and wearables provide viewers with more immersive and interactive experiences than ever before.
Smart stadiums and venues now offer network connectivity for fans via WiFi, Bluetooth and a number of other digital services. Along with this technology, the games are becoming more reliant on critical applications to help provide this experience to those onsite and around the world.
Reliable WiFi is always an issue at large scale events with users wanting to do and see the games while sharing content in real-time. Korea Telecom will be delivering the first broad-scale 5G network for the games and paired with Intel 5G technologies that will enable attendees to engage in a variety of experiences at the Winter Olympics this year.iii In addition, NBC plans on live streaming 1,800 hours of the Winter Olympics and broadcasted 1,000 hours at the Winter Olympics in 2014.
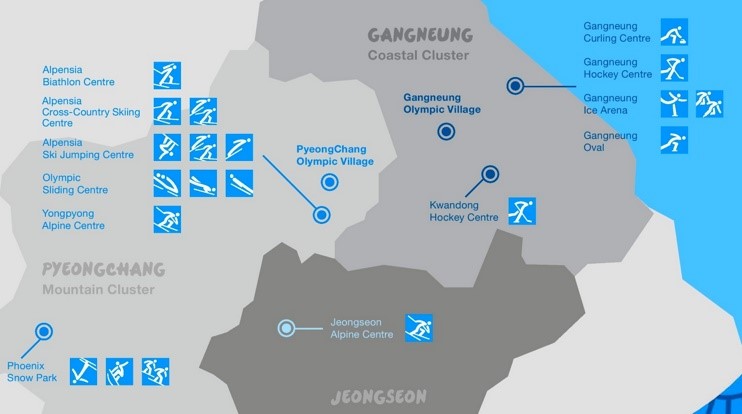 Figure 1: Olympic Venues / Source ontheworldmap.com
Figure 1: Olympic Venues / Source ontheworldmap.com
Venues
PyeongChang Mountain Cluster
Gangneung Coastal Cluster
Targets
- International Olympic Committee (IOC)
- Carriers
- Service Providers
- Sponsors
- Partners
- Suppliers
- Subcontractors
- Venues
- Athletes
- Spectators
Reasons for Concern
Radware’s Emergency Response Team and researchers are currently assessing the Winter Olympics in PyeongChang. The Winter Olympics creates a great platform for hacktivists and cyber criminals to spread a message, make profit or create disruption. Today, it is very easy for low-level threat actors to carry out large-scale and disruptive attacks. Toolkits and attack services are widely available for purchase on the clear and darknet.
Today, most cybercriminals and hacktivist focus on identity theft by spreading malicious software designed to harvest and steal personal information. Often it is the technologies designed to enhance the spectators’ experience, such as Wi-Fi, Bluetooth and other digital services that are exploited to harvest this information from attendees.
 Figure 2: Access Points/Source: nowpyeongchang.com/wifi
Figure 2: Access Points/Source: nowpyeongchang.com/wifi
One of the biggest concerns about the Olympics is protecting critical applications and networks that support the event. Broadcast networks, industrial control systems, operational networks and other related systems are all at risk.
Mobile devices are also at risk for athletes and viewers. Athletes are targeted for espionage and spectators are targeted for personal information and financial credentials. Providing spectators and athletes with connectivity is a double-edge sword. Connected venues become a bring-your-own-device nightmare for event management and wireless network operators. Open Wi-Fi networks also present one of the biggest attack vectors for network- and malware-based attacks. Criminals know that visitors are reliant on Wi-Fi access points, making them an easy target.
Common types of attacks at the Olympics may include:
- Compromising unsecure and vulnerable access points
- Deploying evil twins or fake cell phone towers
- Spreading malware via phishing
- Data mining using fake pop ups, text messages or spoofed websites
- Denial-of-service attacks on critical applications
- Injection attacks aimed at stealing data
Several organizations associated with the games have already been targeted by spear phishing attacks. Hackers have already begun targeting the Olympics with Fancy Bear claiming to have compromised emails from the IOC.iv In 2016, Fancy Bear also was suspected to be behind the hack targeting WADA (
World Anti-Doping Agency).
 Figure 3: Fancy Bear post related to IOC emails
Figure 3: Fancy Bear post related to IOC emails
Threat Actors
CrowdStrikev and McAfeevi both have reported a spear phishing campaign suspected of targeting those involved or supporting the 2018 Winter Olympics. The email came from a spoofed message with the senders address belonging to South Korea’s National Counter-Terrorism Center but was sent from an IP address in Singapore. ThreatConnectvii has also reported that they have identified two domains that appear to be spoofing the UK Anti-Doping website.
Early in January, Talos also reported about malicious activities from Group 123. In several campaigns in 2017, Group 123 was seen targeting South Korean users with a spear phishing email containing a malicious document designed to install and execute ROKRAT, a remote administration tool, RATviii.
Attack Vectors
Phishing
A digital attempt to obtain sensitive information from a victim by using a malicious email or website. The attacker solicits personal information by posing as a trustworthy organization or the company itself. These attempts are either sent out to everyone in the company or designed to specifically target key associates. Once an associate falls victim to these the hacker will then have the sensitive information required to gain access to certain systems.
 Figure 4: Dnstwist – source: https://github.com/elceef/dnstwist
Figure 4: Dnstwist – source: https://github.com/elceef/dnstwist
Malicious Domains
Malicious domains are registered domains designed for malicious intent. Users are normally directed to these sites via fake giveaways for tickets promoted on social media. Bad domains look to hijack names of cities, venues or events to trick users via typo squatting into entering their credentials by spoofing the content of the original website. More advanced forms of malware contain domain-generating algorithms (DGAs) to evade solutions based on signatures or blacklisting.
Denial-of-Service
Considering the high volumes of traffic service providers will cope with, it would not take a sophisticated attack to take an ISP down; a massive DDoS attack via a reflective method in combination with the natural peaks of traffic may be enough to cause service degradation. Denial-of-service attacks can be generated via an IoT botnet such as Mirai. Hackers can leverage multi-vector techniques by combining network floods with various low and slow attacks and even encrypted distributed denial-of-service attacks to cause an outage. A consumption spike might appear as a DDoS attack. Many DDoS mitigation solutions are rate-based and will drop traffic above a certain threshold. Behavioral algorithms not only make an accurate distinction between attack and legitimate user traffic but also instantly detect unknown attacks at a minimal false positive rate.
Application Attacks
Hacktivists and criminals will launch application attacks like SQL injections, password cracking, cookie poisoning, cross-site scripting*, session highjacking and others in an attempt to steal Olympic and spectator data. Information on the attendees, sponsors, or athletes can be quickly monetized or publicly used. Criminals will also use fake applications and websites to target patrons.
* Cross-site scripting against vulnerable webpages - injecting a client-side script into the user’s browser.
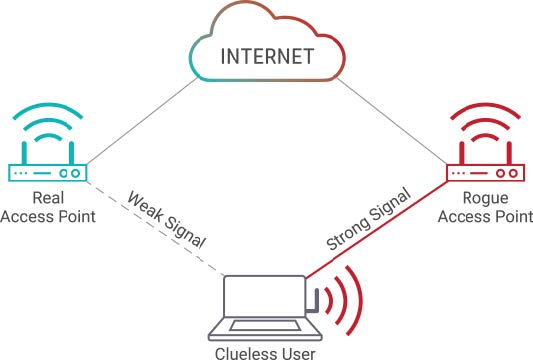
Compromised Access Points – Risk of MITM
As part of their preparations, hacktivists and cyber criminals have likely already assessed access points and their vulnerabilities across the Olympic venues. They will set up fake access points to intercept and manipulate their victims browsing and to steal passwords, credit cards, PII and other sensitive information. A common MITM tactic using malicious access points is to name fake access point as the same name of the legitimate access points. Once a user is connected, malware can be injected onto their device.
ATM Skimmers
Criminals will be deploying skimmers on ATMs and point-of-sale systems at the 2018 Winter Olympics. It allows hackers to record the ATM user information and later sell it for profit. The larger the crowd, the higher number of potential victims.
 Figure 5: ATM Skimmers
Figure 5: ATM Skimmers
Mobile Phones
There is a high risk for targeted attacks against high profile visitors at the 2018 Winter Olympics. Visitor devices could be easily targeted by cyber criminals at the games. Fake charging stations or compromised access points can allow an attacker to gain root access into a device. Once infected, devices can perform tasks like record audio and video, take photos, send text messages, open webpages, steal user data, delete files, launch denial-of-service attacks via HTTP floods and perform web injections.
How to Prepare
Technology can provide a more immersive and rewarding experience for fans but also creates problems and security risks for those managing the event. Those that sponsor, support or supply the Olympics should understand the risk and their exposure. Here are suggestions for both attendees and those hosting the 2018 Winter Olympics.
Attendees/Users: How to Prepare for the Winter Olympics
- Ensure your phone is updated with the latest operating system
- Disable Bluetooth when not in use
- Disable Wi-Fi when not in use
- Use the official event Wi-Fi when device is in use
- Always use a VPN
- Have RFID shields to protect RFID cards
- Be careful when using ATMs – Understand how to spot and avoid card skimmers gathering data.
- Exercise caution when presented with pop ups while browsing
- Avoid Olympic related scams delivered via email.
Event Operators: How to Prepare for the Winter Olympics
Radware recommends that operators review their network between events and inspect networks as necessary in order to defend the threats presented during the Olympics.
- Ensure hardware is updated
- Conduct audits of the network between games
- Access Control List (ACL) – Filtering network traffic
- Use load balancing for traffic distribution
- Have network and application protection to detect, mitigate and report attacks
Effective DDoS Protection Essentials
- Hybrid DDoS Protection - On-premise and
cloud DDoS protection for real-time
DDoS attack prevention that also addresses high volume attacks and protects from pipe saturation
- Behavioral-Based Detection - Quickly and accurately identify and block anomalies while allowing legitimate traffic through
- Real-Time Signature Creation - Promptly protect from unknown threats and zero-day attacks
- A Cyber-Security Emergency Response Plan - A dedicated emergency team of experts who have experience with Internet of Things security and handling IoT outbreaks
For further network and application protection measures, Radware urges companies to inspect and patch their network in order to defend against risks and threats.
Effective Web Application Security Essentials
- Full OWASP Top-10 coverage against defacements, injections, etc.
- Low false positive rate – using negative and positive security models for maximum accuracy
- Auto policy generation capabilities for the widest coverage with the lowest operational effort
- Bot protection and device fingerprinting capabilities to overcome dynamic IP attacks and achieving improved bot detection and blocking
- Securing APIs by filtering paths, understanding XML and JSON schemas for enforcement and activity tracking mechanisms to trace bots and guard internal resources
- Flexible deployment options - on-premise, out-of-path, virtual or cloud-based
Under Attack and in Need of Expert Emergency Assistance? Radware Can Help
Radware offers a service to help respond to security emergencies, neutralize the risk and better safeguard operations before irreparable damages occur. If you’re under DDoS attack or malware outbreak and in need of emergency assistance,
contact us with the code "Red Button."
- i http://www.computerweekly.com/news/2240168945/Cyber-attacks-launched-at-London-2012-Olympic-Games-every-day
- ii http://www.silicon.co.uk/security/rio-olympics-ddos-attacks-196998?inf_by=5a68339b671db85b2d8b4a7b
- iii https://newsroom.intel.com/editorials/intel-power-5g-network-2018-olympic-games/
- iv https://fancybear.net/pages/wada-vs-ioc.html
- v https://www.crowdstrike.com/blog/malicious-spear-phishing-campaign-targets-upcoming-winter-olympics-in-south-korea/
- vi https://securingtomorrow.mcafee.com/mcafee-labs/malicious-document-targets-pyeongchang-olympics/
- vii https://www.threatconnect.com/blog/duping-doping-domains/
- viii http://blog.talosintelligence.com/2018/01/korea-in-crosshairs.html