Radware’s cyber threat intelligence (CTI) team has observed significant advancements in Iranian influence operations throughout 2024.
Download now
Radware’s cyber threat intelligence (CTI) team has observed significant advancements in Iranian influence operations throughout 2024. It assesses with high confidence that the scale of these operations will significantly grow through the upcoming U.S. elections. These developments pose increased risks to the integrity of these elections, necessitating a reevaluation of current misinformation and disinformation defense strategies.
Key Attack Insights:
- As part of its foreign policy, Iran attempts to manipulate public opinion through automated bots that spread misinformation by pretending to be real social media influencers.
- As U.S. elections approach, these influence operations are expanding from targeting Israelis to focusing on Americans (see Figure 1).
- Iranian actors are leveraging advanced AI technologies to generate convincing content, including deep fake videos and multilingual posts, significantly increasing the scale and sophistication of their campaigns.
- The operations employ a cross-platform strategy, establishing presence across multiple social media services to increase credibility and reach, making containment and detection more challenging.
- Iranian bot operators employ sophisticated TTPs, including the use of proxy IPs, AI-generated content and profiles, cross-platform coordination, and exploitation of current events, making their operations increasingly difficult to detect and counter.
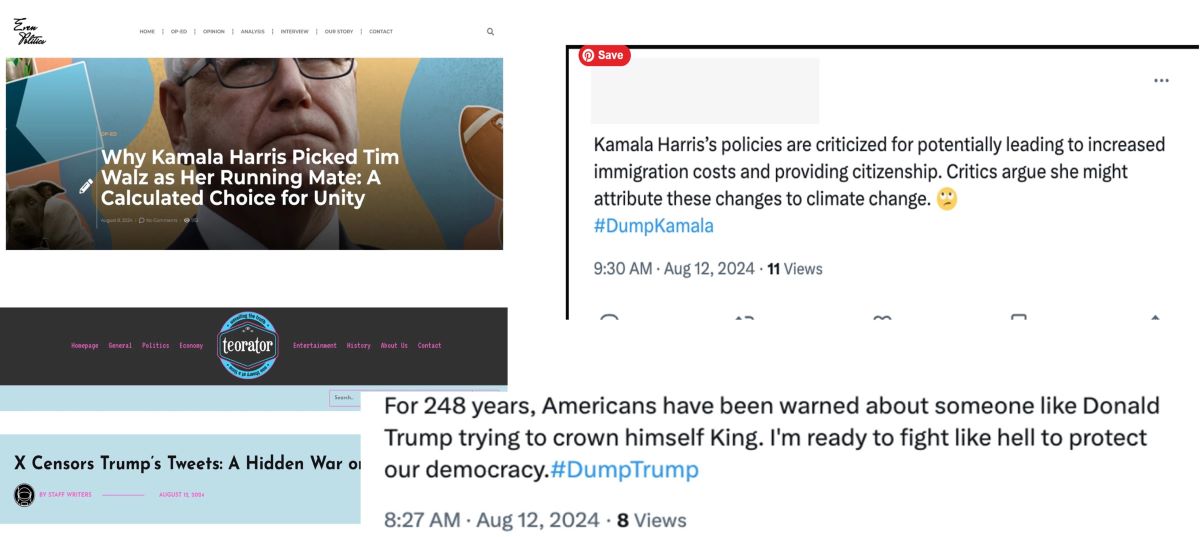 Figure 1: Examples of AI-generated fake news sites and social media botnet tweets captured by OpenAI.
Figure 1: Examples of AI-generated fake news sites and social media botnet tweets captured by OpenAI.
Bot Operations TTP (Tactics, Techniques, and Procedures)
Operation architecture:
- Iranian operators employ specialized proxy services that make their bot traffic appear to originate from residential homes and mobile devices within the targeted country. This technique allows the bots to mimic the online behavior of genuine local users, significantly increasing the difficulty of detection and enhancing the credibility of their influence operations.
Account Management and Structure: Use of a tiered account system
- High-quality "avatar" accounts for direct interaction and content creation
- Larger numbers of lower-quality accounts or bots for amplification and engagement
- Fake accounts to manage Pages and post content [2] [4]
Content Generation and Manipulation: AI-powered content creation
- Use of AI models to generate and rewrite comments in multiple languages
- Creation of AI-generated newsreaders on YouTube
- Rapid adaptation of content to current events and emerging issues [1] [3]
Cross-Platform Tactics: Multi-platform presence and coordination
- Operation of fake news websites posing as both progressive and conservative outlets
- Coordinated posting and sharing across multiple social media platforms
- Driving traffic from social media to external websites [1] [4]
Amplification and Visual Manipulation:
- Use of bots to amplify specific viewpoints (e.g., pro-Russia views on Ukraine war) [3]
- Creation of AI-generated profile photos for fictitious personas using Generative Adversarial Networks (GANs) [3]
Engagement and Recruitment: Direct user interaction
- Messaging real users for recruitment or manipulation
- Collecting personal details through fake "volunteer" forms [2]
Public Opinion Manipulation Operation (Step by Step)
Part 1: Pre-attack Preparation
Account Acquisition:
- Create new social media accounts using bots or purchase social media accounts with established credibility.
- Use AI-generated profile photos for fictitious personas, often created using Generative Adversarial Networks (GANs) [3].
Fake Website Creation:
- Establish fictitious news websites with distinct branding [3].
- Use anonymization techniques to hide the true origin of these sites.
Cross-Platform Presence:
- Establish a presence for fake entities across multiple internet services, including Facebook, YouTube, Telegram, and Twitter (now X) [3].
Part 2: Building Reputation
Content Generation:
- Use AI tools to generate large volumes of non-political content [3].
- Create AI-generated newsreaders on YouTube [3].
- Generate short comments in English and Spanish using AI models [1].
Amplification Techniques:
- Use a network of lower-quality accounts or bots for amplification [2].
- Engage in coordinated posting and sharing across multiple platforms.
Local Engagement:
- Attempt to engage with local audiences through targeted content.
Part 3: The Attack
Disinformation Dissemination:
- Publish AI-generated articles on U.S. politics and global events on websites posing as progressive and conservative news outlets to gain and establish digital reputation and credibility [1].
- Use AI-generated newsreaders on YouTube to criticize specific politicians or policies [3].
Exploitation of Current Events:
- Rapidly adapt narratives to exploit emerging issues or crises.
Targeted Messaging:
- Tailor content for specific audiences to maximize impact.
Deep Fake Deployment:
- Create and disseminate deep fake videos of political figures.
Cross-Platform Amplification:
- Share and amplify content across multiple platforms to increase reach and credibility.
- Use the network of bots and fake accounts to engage with and further spread the disinformation.
“Tears of War” Case Study
The "Tears of War" network, as described in a recent report from Israeli think tank The Institute of National Security Studies, is an Iranian influence operation that emerged after the outbreak of the "Swords of Iron" war (which began on October 7, 2023). Here are the key details...