Threat groups launch a five-day—and counting—politically motivated cyberattack campaign that includes government sites, airports and the Vienna Stock Exchange.
Download nowThreat groups launch a five-day—and counting—politically motivated cyberattack campaign that includes government sites, airports and the Vienna Stock Exchange.
Overview
- Pro-Russian threat actors NoName057(16) and OverFlame have launched a series of DDoS attacks on Austrian targets.
- The attacks are presumably connected to the Russian-Ukrainian conflict, although NoName057 claims they “decided to visit Austria again to check on cybersecurity ahead of the upcoming elections.”
- The attack campaign started on September 16 and continues against over 40 targets including government sites, airports, financial services and Wiener Borse.
Motivation
According to a NoName057 Telegram message, motivation is associated with the upcoming Austrian elections: “On September 29, Austrian citizens will elect members of the 28th National Council, the lower house of the country's parliament. According to polls, the far-right Freedom Party of Austria (FPÖ) is expected to lead with 27 percent of the vote and form the largest faction in parliament. In second place, the opposition Social Democratic Party of Austria (SPÖ) is projected to come in with 23% of voter support. In third place is likely to be the Austrian People's Party (ÖVP) with 22% support, which is part of the current ruling coalition. We decided to visit Austria again to check on cybersecurity ahead of the upcoming elections. As it turns out, nothing has changed since our last visit."
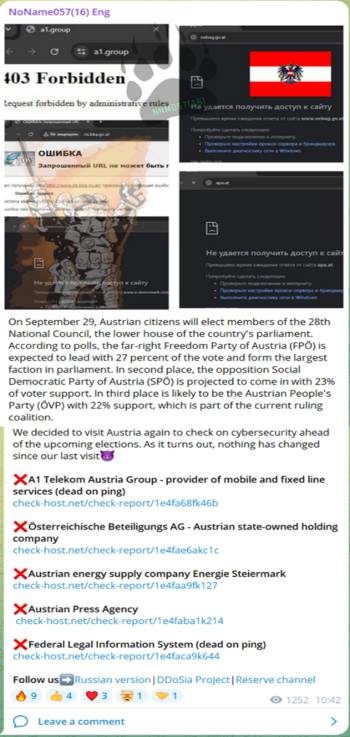 Figure 1: NoName057 claims attacks on Austrian sites and provides the motivation through Telegram
Figure 1: NoName057 claims attacks on Austrian sites and provides the motivation through Telegram
Threat Actors
NoName057(16) is a pro-Russian hacker group known for its cyberattacks on Ukrainian, American and European websites of government agencies, media and private companies. It is regarded as a well-organized hacktivist group with over 2.5 years of experience targeting countries that support Ukraine or speak badly about Russia.
OverFlame is a relatively obscure hacktivist group known for targeting government institutions and corporations, particularly in Europe and North America. The group specializes in DDoS attacks and website defacements, often motivated by anti-government and anti-corporate sentiments. OverFlame operates through underground forums and encrypted messaging platforms, where they coordinate their attacks and recruit new members.
It is common to see like-minded threat actors make ad-hoc alliances and collaborate on campaigns to increase their impact.
Attack Tools
Threat actors have mastered their ability to generate highly evasive and sophisticated HTTPS flood attacks that are hard to detect and mitigate.
The tool used by NoName057, the major threat actor in this campaign, is a crowdsourced botnet project named DDOSIA. The project leverages politically driven hacktivists willing to download and install a bot on their computers to launch denial-of-service attacks. Project DDOSIA, however, raises the stakes by providing financial incentives for the top contributors to successful denial-of-service attacks.

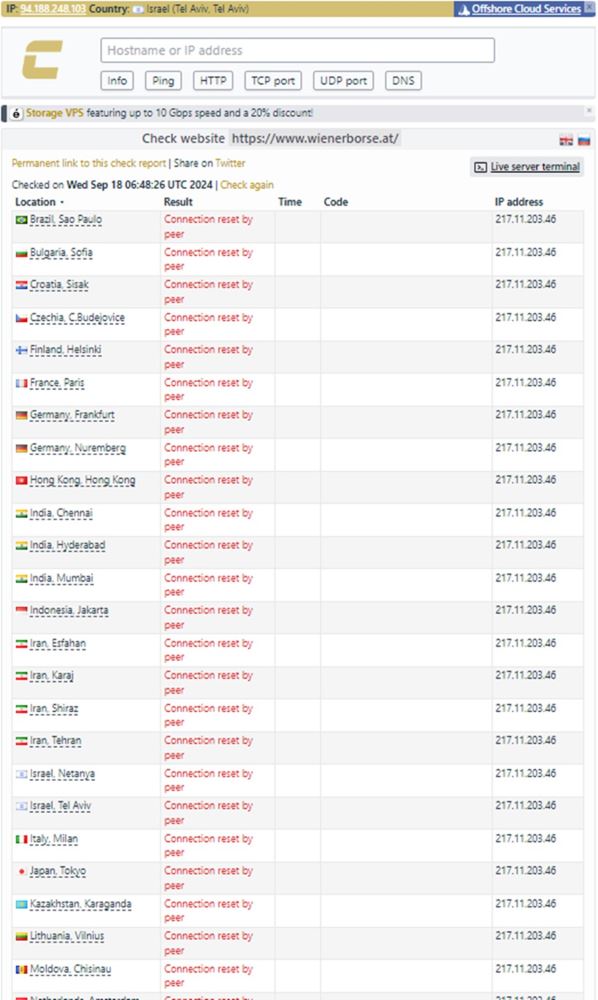
Figure 2: NoName057 claims an HTTPS flood attack on the Wiener Boerse AG managing the stock exchange in Vienna and Prague. The Check Host page shows the victim resources were offline
Attack Timeline
Claiming Actors
Targeted Industries
EFFECTIVE DDOS PROTECTION ESSENTIALS
Real-Time Signature Creation - Utilize Radware's ability to promptly create and deploy signatures to protect against emerging threats and zero-day attacks.
Cross-Platform Monitoring - Employ Radware's comprehensive monitoring tools to track influence operations across various digital channels.
Rapid Response Capabilities - Leverage Radware's 24/7 Emergency Response Team to swiftly address and mitigate emerging threats.
Behavioral-Based Detection - Leverage Radware's advanced behavioral analysis to quickly and accurately identify and block anomalous bot activity while allowing legitimate traffic.
AI-Powered Content Analysis - Implement Radware's AI-driven solutions to detect and mitigate sophisticated disinformation campaigns across multiple platforms.
For further network and application protection measures, Radware urges companies to inspect and patch their network to defend against risks and threats.
EFFECTIVE WEB APPLICATION SECURITY ESSENTIALS
Low false positive rate - using negative and positive security models for maximum accuracy
Auto-policy generation - capabilities for the widest coverage with the lowest operational effort
Bot protection and device fingerprinting - capabilities to overcome dynamic IP attacks and achieve improved bot detection and blocking
Full OWASP Top-10 – coverage against defacements, injections, etc.
Flexible deployment options – on-premises, out-of-path, virtual or cloud-based
Securing APIs - by filtering paths, understanding XML and JSON schemas for enforcement, and using activity tracking mechanisms to trace bots and guard internal resources