
A phishing attack is a deceptive and malicious attempt to trick individuals into revealing sensitive information, such as passwords, credit card numbers, or personal details, by impersonating a trustworthy entity.
Fraudsters often employ various means, such as emails, text messages, or phone calls to masquerade as legitimate organizations or individuals, creating a false sense of urgency or importance to coerce victims into divulging confidential data. These attacks are designed to exploit human psychology and vulnerabilities through cleverly crafted messages or communications, often utilizing social engineering techniques to manipulate and deceive unsuspecting targets.
Phishing attacks constitute a significant portion of cyberthreats, comprising a substantial percentage of overall cyberattacks. According to recent statistics, approximately 91% of attacks begin with a phishing email to innocent victims. 32% of successful data breaches involve phishing techniques. This demonstrates the prevalent use of phishing as a preferred method for cybercriminals seeking unauthorized access to systems and information. This success rate underscores the need for enhanced awareness, education, and cybersecurity measures to mitigate the risks posed by phishing attacks.
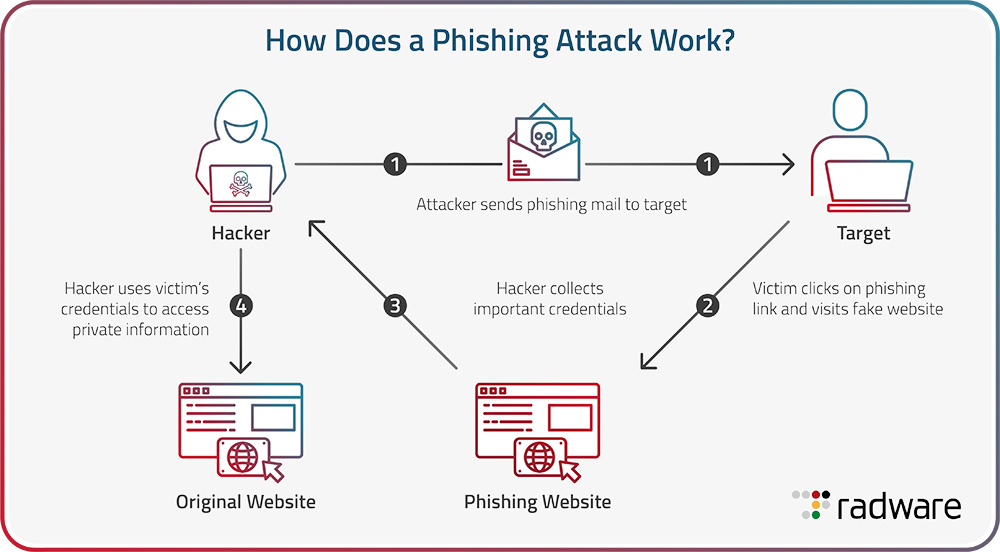
A phishing attack is a carefully designed cybercrime that involves tricking individuals or organizations into divulging sensitive information or performing actions that compromise their security. The process typically involves these steps:
Use of Social Engineering Tactics: Phishing attacks heavily rely on social engineering techniques to manipulate human behavior. This might involve playing on emotions like fear, curiosity, or greed, or creating a sense of urgency to coerce individuals into responding as desired.
Research and Target Selection: Phishers conduct research to identify potential targets and tailor their attack accordingly. They may target specific organizations, or individuals based on the value of the information they possess or their susceptibility to deception.
Creation of a Credible Impersonation: Phishers design communications that impersonate trustworthy entities like banks, government agencies, social media platforms, or reputable companies. They craft emails, messages, or websites that closely resemble the real ones, utilizing logos, branding, and language to create a sense of legitimacy.
Delivery of the Phishing Message: Phishers send out phishing messages through various channels like email, SMS, social media, or phone calls. The message often contains urgent or enticing content, prompting recipients to take immediate action, such as clicking a link, downloading an attachment, or providing personal information.
Deceptive Links or Attachments: The phishing message typically includes links to fraudulent websites or malicious attachments. These links may redirect victims to a phishing site designed to collect login credentials, financial data, or install malware on their devices.
Data Collection: If the victim interacts with the phishing site, it may prompt them to enter sensitive information, such as login credentials, credit card numbers, or social security numbers. The phisher collects this data for nefarious purposes.
Exit and Covering Tracks: After collecting the desired information or deploying malware, the phisher may redirect the victim to a legitimate site or display a false error message to avoid suspicion. They cover their tracks to evade detection and continue their malicious activities.
Malware Deployment: In some cases, the phishing link or attachment may deliver malware to the victim's device, compromising their system's security. The malware can be used for various malicious activities like stealing data, recording keystrokes, or enabling remote control of the compromised device.
Here are some common types of phishing attacks and their associated dangers:
Spear Phishing Attack: Spear phishing is a highly targeted form of phishing, where attacks are tailored to specific individuals or organizations. Phishers use research to gather personal information about the target, making the phishing attempt more convincing. The danger lies in the personalized nature of the attack, often leading to a higher success rate compared to standard phishing attempts which consists of generic messages sent to a broader audience without personalization.
Email Phishing Attack: Email phishing is one of the most prevalent forms of phishing, involving the use of deceptive emails to trick recipients into revealing personal information, clicking on malicious links, or downloading malicious attachments. These emails often imitate reputable entities such as banks, government agencies, or well-known companies. The danger lies in the widespread use of emails, making it easy for attackers to target a large number of individuals and organizations.
Vishing Attack: Vishing involves using phone calls or VoIP (Voice over Internet Protocol) to deceive individuals into revealing personal or financial information. Attackers may impersonate legitimate organizations, government agencies, or banks to create a sense of urgency or importance. Convincing verbal communication can make victims likely to divulge sensitive details. These attacks can lead to identity theft, financial fraud, or unauthorized access to accounts.
Whale Phishing Attack: Whale phishing targets high-profile individuals within an organization, such as executives or high-ranking officials, seeking unauthorized access to valuable information or financial transactions. Attackers craft emails appearing to come from trusted colleagues or superiors, urging the recipient to transfer funds, provide confidential data, or take specific actions.
Clone Phishing: Clone phishing involves creating a replica of a legitimate email or communication from a trusted source and sending a modified version to the recipient. The modified version typically contains malicious links or attachments, leading to malware installation or data theft. The deceptive nature of the cloned message makes it challenging for recipients to recognize the threat.
Smishing Attack: Smishing employs SMS or text messages to trick recipients into clicking malicious links or providing sensitive information. These messages often contain urgent requests or offers to entice recipients. The increasing use of mobile devices makes malware installation or financial fraud more likely if victims fall for the scam.
A spoofing attack involves the manipulation of data to falsify the source or origin of a communication. This could include altering email headers, IP addresses, or domain names to make the communication appear to come from a trusted entity. On the other hand, phishing is a broader social engineering technique that involves tricking individuals into divulging sensitive information or performing certain actions (like clicking a link or downloading an attachment) by impersonating a reputable entity. This is achieved through deceptive emails, messages, or calls that exploit human psychology.
While both spoofing and phishing involve deception and manipulation to achieve malicious goals, phishing is a comprehensive approach that encompasses various tactics, including spoofing, to deceive and manipulate individuals.
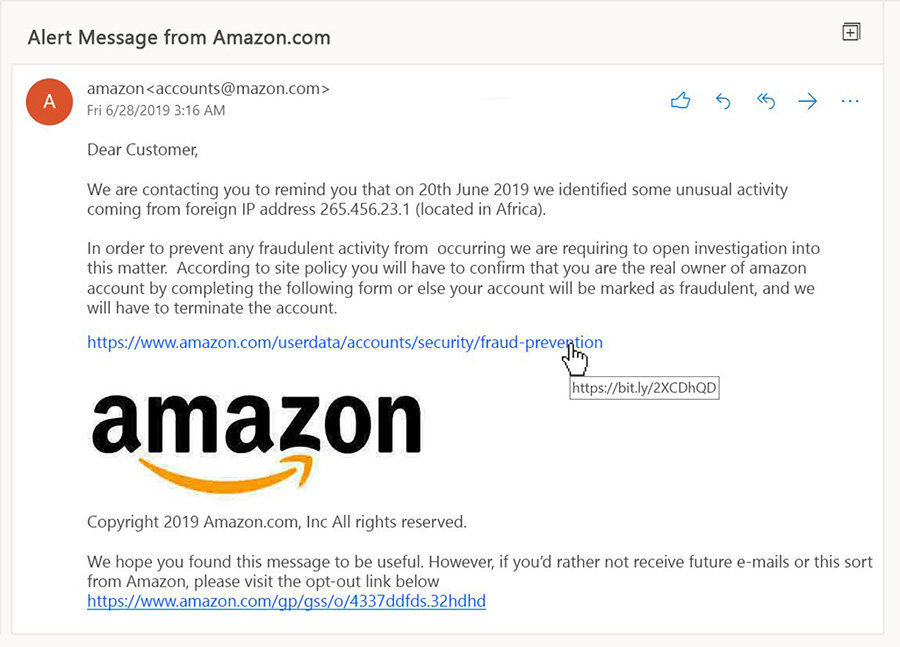
An example of a phishing email from a sender claiming to be Amazon with a sender address “@mazon.com”:
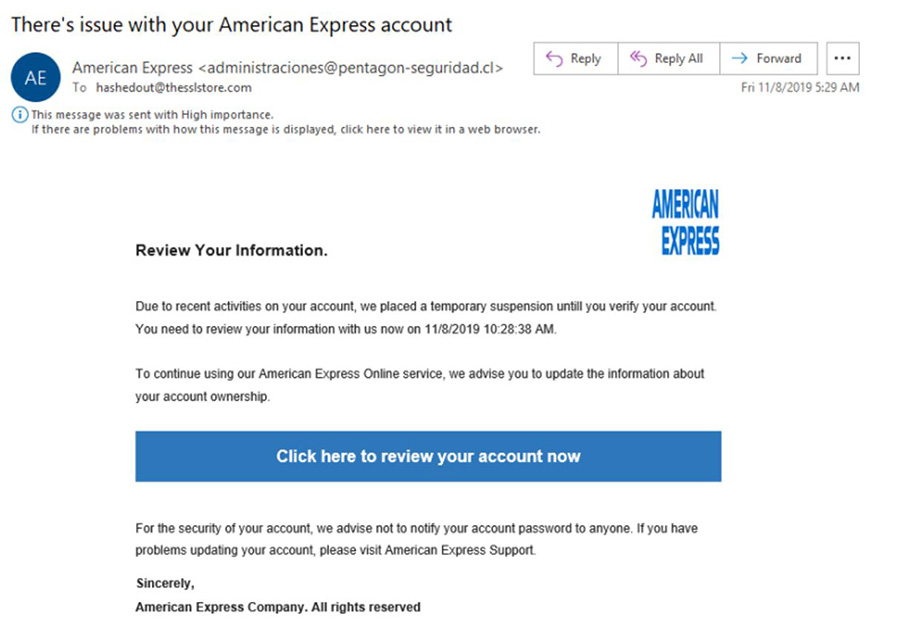
An example of a phishing email claiming to be from American Express:
Recovering from a phishing attack and mitigating potential damage is crucial to minimize the impact and prevent future attacks. Here's a step-by-step guide to assist in the recovery and mitigation process:
Act Quickly and Report the Attack: Speed is of the essence. As soon as you realize you've fallen victim to a phishing attack, report it to your organization's IT or security team, or to the appropriate authorities if it's a personal account. Notify your bank or credit card provider if financial information was compromised.
Change Credentials: Immediately change passwords for all compromised accounts, including email, social media, banking, and any other sensitive accounts. Enable multi-factor authentication (MFA) wherever possible to enhance security.
Seek Professional Help: If the attack is severe or you're unsure about the extent of the compromise, consult a cybersecurity professional or an IT expert to assess the damage and recommend appropriate actions.
Contact Credit Bureaus: Consider placing a fraud alert or credit freeze on your credit reports to prevent the attacker from opening new accounts in your name. Contact major credit bureaus to initiate these measures.
Implement Security Measures: Install reliable and up-to-date security software, firewalls, and email filters to block phishing attempts and other malware. Utilize email authentication protocols like SPF, DKIM, and DMARC to help prevent email spoofing. Additionally, conduct regular security audits to identify vulnerabilities in your systems and processes.
Educate and Train: Regularly educate your team and others about phishing tactics, warning signs, and how to identify suspicious emails, links, or attachments to prevent future attacks in addition to taking regular backups of files to a secure location so that you can restore your data without paying any ransom.
Scan for Malware: Run a thorough antivirus and antimalware scan on your devices to detect and remove any malicious software that might have been downloaded during the phishing attack.
Stay Informed: Keep up to date with the latest phishing trends, attack techniques, and cybersecurity best practices. Awareness is a powerful defense against future attacks.
Here are proactive measures to help prevent phishing attacks and protect against potential threats:
Education and Awareness:
Educate yourself and your team about phishing tactics, red flags, and common attack methods. Regular training and awareness programs can significantly reduce susceptibility to phishing.
Verify Email Sources:
Double-check email sender addresses, especially if the email requests sensitive information or urgent action. Verify the sender's legitimacy before responding or clicking on any links.
Use Email Filters:
Employ email filtering solutions that can detect and quarantine phishing emails before they reach your inbox. Advanced filters can significantly reduce the number of phishing attempts.
Regular Software Updates:
Keep your operating system, antivirus software, browsers, and plugins up to date to ensure they have the latest security patches that can protect against known vulnerabilities.
Secure Website Browsing:
Look for “https://” in the website URL to ensure secure browsing. Avoid entering personal or financial information on websites without this secure protocol.
Implement Multi-Factor Authentication (MFA):
Enable MFA for all accounts, adding an extra layer of security that requires multiple forms of verification to access your accounts.
Use Anti-Phishing Tools:
Consider using anti-phishing solutions, to detect and block phishing attempts in real-time, providing an added layer of security against evolving phishing techniques.
Exercise Caution with Links and Attachments:
Hover over links to preview the URL before clicking. Avoid clicking on suspicious links or downloading attachments from unknown or unexpected sources.
Regular Data Backups:
Back up your important data regularly and store it in a secure location. This ensures that in the event of a successful phishing attack, you can restore your data without paying a ransom.
Be Cautious with Personal Information:
Avoid oversharing personal information on social media or public forums, as attackers often gather information from such platforms to craft targeted phishing attacks.
Report Suspicious Activity:
If you encounter a phishing attempt, promptly report it to your organization's IT department or the appropriate authority to take necessary action and prevent further attacks.
Radware solutions play a crucial role in defending against phishing attacks to provide a comprehensive and multi-layered approach to cybersecurity:
Bot Manager: This solution provides protection from automated threats like bots. Bots are often used in phishing attacks to automate the process of sending out fraudulent emails or messages. By identifying and blocking these bots, Radware can help prevent these phishing attempts.
Cloud WAF Service: This service provides continuously adaptive web application security protection. It can help identify and block phishing attempts by detecting malicious behavior and unauthorized system access.
Client-Side Protection: This solution secures end users from attacks embedded in your application supply chain. Phishing attacks often involve embedding malicious code in applications, which can then be used to steal sensitive information. By protecting the client-side, Radware can help prevent these types of attacks.
API Protection: This solution works in real time to detect and block a broad range of threats. Phishing attacks often involve attempts to exploit vulnerabilities in an organization’s APIs. Radware’s API protection can help prevent this by blocking unauthorized access and data leakage.
DDoS Protection: This solution offers real-time protection for sophisticated DDoS and web security threats. While not directly related to phishing, DDoS attacks can often be used in conjunction with phishing attacks to distract security teams and make the phishing attack more successful.
Threat Intelligence Subscriptions: These subscriptions enhance Radware’s Attack Mitigation Solution and extend its automated, real-time behavioral threat analysis. This allows for preemptive protection against phishing attacks by identifying potential threats before they can cause harm.