On June 10th, 2022, DragonForce Malaysia launched a series of cyberattacks against the government of India and numerous organizations across the country.
Read the Complete Alert
On June 10th, 2022, DragonForce Malaysia launched a series of cyberattacks against the government of India and numerous organizations across the country.
OpsPatuk
OpsPatuk is a new campaign from DragonForce Malaysia. Like all operations this hacktivist group runs, this one is reactionary and in response to the controversial Bharatiya Janata Party (BJP) spokesperson Nupur Sharma condemning the Prophet Muhammad, SAW1. As a result, DragonForce Malaysia, with the assistance of several other threat groups, has begun indiscriminately scanning, defacing and launching denial-of-service attacks against numerous websites in India. More advanced threat actors were observed leveraging current exploits, breaching networks and leaking data.
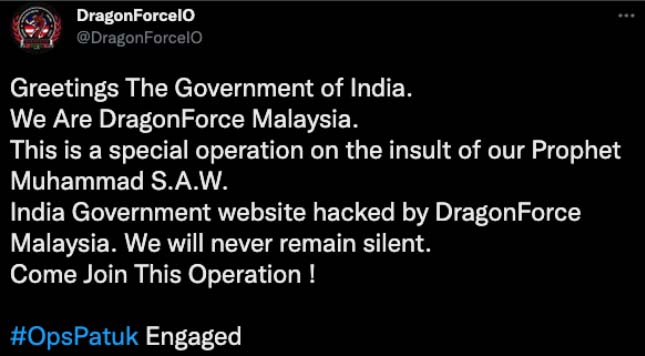 Figure 1: DragonForce Malaysia announcing OpsPatuk on social media
Figure 1: DragonForce Malaysia announcing OpsPatuk on social media
DragonForce Malaysia
The driving force behind #OpsPatuk is a hacktivist group known as DragonForce Malaysia. The group is a known pro-Palestinian hacktivist group located in Malaysia and has been observed working with several threat groups in the past, including the T3 Dimension Team and ReliksCrew. DragonForce Malaysia has a website and a forum where threat actors conduct most of their announcements and discussions. The group also has a Telegram channel, but most content is replicated throughout the forum and other social media platforms, including TikTok.
Before #OpsPatuk, DragonForce Malaysia targeted organizations and citizens across Israel with #OpsBedil, #OpsBedilReloaded and #OpsRWM (Raids Without Mercy).
Recent Attacks
Members of DragonForce Malaysia, along with other threat groups, began targeting numerous organizations and government resources in India with defacements, denial-of-service attacks and data leaks on June 10, 2022, as part of OpsPatuk. The operation is still ongoing at the time of publication.
DDoS Attacks
As seen in previous operations, DragonForce Malaysia again uses well-designed advertisements that list information about targets to entice followers to join the operation. The events are announced in the DragonForce Malaysia forums and shared through social platforms. Denial-of-service campaigns from the threat group are typically announced less than 24 hours in advance. In addition to the official attacks, unannounced denial-of-service attacks are to be expected by “lone-wolfs” as the operation progresses.
DragonForce Malaysia is not considered an advanced or a persistent threat group, nor are they currently considered to be sophisticated. But where they lack sophistication, they make up for it with their organizational skills and ability to quickly disseminate information to other members. Threat actors launching denial-of-service attacks during #OpsPatuk have been leveraging DragonForce Malaysia's standard toolset, including but not limited to, Slowloris, DDoSTool, DDoS-Ripper, Hammer, and several other scripts generally found in open source repositories such as GitHub. To this date, the threat group has not been seen leveraging IoT botnets.
1 Muslims follow the name of Muhammad by the Arabic benediction sallallahu 'alayhi wa sallam, meaning Peace be upon him, abbreviated as "SAW" or "PBUH".