This data-driven report provides insights into DDoS attacks claimed by hacktivists between February 18 and April 18, 2023.
Download a Copy Now
This data-driven report provides insights into DDoS attacks claimed by hacktivists between February 18 and April 18, 2023. The report aims to provide a quantitative answer to questions such as:
- Who is claiming the most attacks?
- Which groups are reposting and trying to get attention while claiming others’ attacks?
- Which countries were most attacked?
- Which hacktivist groups were targeting which countries?
- Which categories of websites were most targeted?
Insights
- Killnet, the group most prominently covered in the media and suspected of most hacktivist DDoS activity, did not make the top 15 of hacktivists claiming DDoS attacks in the last two months.
- NoName057(16), who does not want to be associated with Killnet, is by far the most active DDoS hacktivist amongst the politically driven, pro-Russian hacktivists.
- Anonymous Sudan, Mysterious Team and Team Insane PK are responsible for most of the religiously driven DDoS activity and rank 2, 3 and 4 in the global hacktivist activity charts.
- Israel was the most attacked country, followed by India, Poland, Australia, United States and Germany. Attacks on Israel, India and Australia were religiously driven attack campaigns under the battle tags #OpIsrael/#OpsPetris, #OpIndia and #OpAustralia.
- Poland, US and Germany were political, Russo-Ukraine conflict driven attack campaigns.
- Globally, business and government websites were most targeted, followed by travel, education, financial services, military and health care.
- Israel was targeted predominantly by Mysterious Team, Anonymous Sudan, Team Insane PK and Anon Cyber Vietnam.
- Australia was predominantly targeted by Mysterious Team and Anonymous Sudan.
- India was targeted predominantly by Team Insane PK and Mysterious Team, followed by Anonymous Sudan and Anon Cyber Vietnam. Financial services and government websites represented over 50% of the total hacktivist DDoS activity.
- Poland is the only country ranking in the top 5 most targeted countries that was targeted by pro-Russian hacktivists in attacks relating to the Russo-Ukrainian war.
- NoName057(16) stuck to purely politically motivated attacks.
- While Anonymous Sudan was declared a member of Killnet back when it was targeting Denmark and Sweden, its motivations were mainly religious and not political. The DDoS activity by Anonymous Sudan was predominantly driven by religion, with some exceptions where it returned a favor for Russian hacktivists.
- Anonymous Sudan predominantly attacked Sweden, Denmark, Israel, France and Australia. While there might be doubts about the alignment of Anonymous Sudan to the Russian government, their attack motives and patterns suggest a religiously motivated group rather than a politically motivated one.
- Passion Group, which started life as a pro-Russian hacktivism group supporting the political narrative of Killnet, is since 2023 primarily driven by its economic objective. Passion Group likes to target high profile organizations to demonstrate their botnet's capabilities and promote their DDoS-for-hire services within the pro-Russian hacktivist community.
- Passion has been targeting a slew of large, US-based cloud organizations, including Facebook, Uber, Nasa, Reddit, WSJ, Amazon and Google. The group occasionally aligns their attacks with the campaigns of other pro-Russian hacktivists, but that is believed to be mainly in support of their economic objectives and, in lesser part, to support the political narrative of the pro-Russian hacktivists' campaigns.
Hacktivism
Hacktivism is a complex phenomenon that can be motivated by various factors, including religious and political beliefs. While hacktivists may have different motivations and methods, they all share a desire to use technology to advance their cause and to challenge those they believe are acting against it.
Hacktivists use a variety of tactics to achieve their goals, and the specific tactics they use depend on their motivations and the resources they have at their disposal. Their methods are constantly evolving as new technologies and platforms emerge. While some tactics may be illegal or unethical, hacktivists argue that they use their skills to promote social or political change and hold powerful organizations and governments accountable for their actions.
Some common tactics used by hacktivists:
- Denial-of-service attacks: This involves overwhelming a website or online service with traffic, making it unavailable to users. Hacktivist groups use DDoS attacks to disrupt websites of organizations and governments they oppose. Since the start of the conflict in Ukraine, DDoS attacks have been performed on both sides of the conflict with Ukrainian hackers targeting Russian organizations while pro-Russian hackers targeted any government or organization that might demonstrate support to Ukraine.
- Website defacements: Hacktivists may hack into a website and replace its content with their own messages or images. This tactic is often used to express dissent or to raise awareness of a particular issue. Pro-Muslim hacktivists haven been claiming a good number of defacements in recent attacks against Israeli business and government websites during #OpIsrael and #OpsPetir.
- Data breaches: Hacktivists may gain unauthorized access to an organization's computer systems and steal sensitive information, such as personal data or confidential documents. They may then release this information publicly or use it to further their political or religious goals. Over the last few months, pro-Russian and pro-Muslim hacktivists have claimed a large number of data breaches and credential compromises. While many of these will most likely be fake breaches leveraging old and previously stolen documents from prior data leaks, this remains hard to prove, and the sheer volume of claimed breaches makes it impossible to assess the success of the hacktivists.
- Media campaigns: Hacktivists may use social platforms like Telegram, Twitter or Facebook and media to spread their message and raise awareness for their cause. They create viral campaigns or use hashtags to amplify their message and reach a wider audience. DragonForce Malaysia has proven to be very effective in their communications, building a community and very proficient in the graphical designs for their operations.
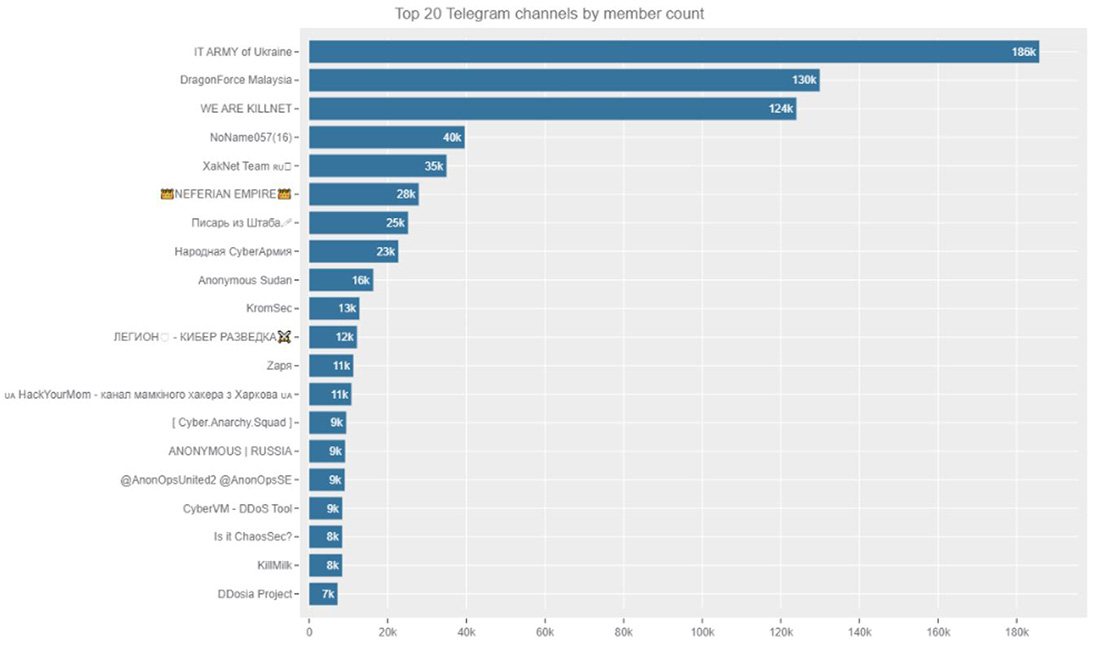 Figure 1: Top 20 Telegram channels followed by Radware Research (ranked by member count)
Figure 1: Top 20 Telegram channels followed by Radware Research (ranked by member count)
PATRIOTIC HACKTIVISTS
Shortly after the start of the invasion of Ukraine, the first vice prime minister of Ukraine, Mykhailo Fedorov, announced the creation of a volunteer cyber army to fight Russian propaganda and protect the interests of Ukraine in cyberspace. The IT Army of Ukraine mainly coordinates its efforts via Telegram and Twitter. The IT Army of Ukraine Telegram channel gathered over 186 thousand members in a little over a year. It became one of Telegram's largest active hacker channels, surpassing by a good margin the DragonForce Malaysia channel, known to be one of the largest and most social hacktivist groups before the start of the invasion.
The emergence of pro-Russian hacktivists was a reaction to the Western cyber response against the aggression of Russia’s invasion of Ukraine. Western hackers volunteering for the IT Army of Ukraine started conducting attacks against Russian targets, joined by factions of Anonymous under their battle tag #OpRussia, on the first day following the invasion by Russia. As a reaction, several opposite groups formed, amongst them a faction of Anonymous calling itself “Anonymous Russia.” Soon a cluster of pro-Russian hacktivist allies and affiliates started to form around a group called Killnet. After little more than a year, the Killnet Telegram groups generated a following that matched DragonForce Malaysia but were still only two-thirds of the following generated by IT Army of Ukraine in the same timeframe. Other notable pro-Russian hacktivist groups generated much lower following compared to the largest groups.
NoName057(16), a pro-Russian hacktivist group who does not want to be associated with Killnet, generated a respectable following of 40,000 members and its DDosia volunteer botnet project generated 7,000 members. Killnet cluster members such as XakNet Team and Zarya respectively generated 35,000 and 11,000 members. The leader of Killnet, KillMilk, was able to create a following of 8,000 members on his personal Telegram channel. Anonymous Russia generated a following of 9,000 members and lagged seriously behind the larger patriotic hacktivist groups. Recently, the head of Anonymous Russia, Raty, was apprehended by the Belarusian authorities after KillMilk, the leader of Killnet, exposed their identity. The original Telegram channel of Anonymous Russia was completely wiped and replaced by a new channel with the same name. Killnet announced that he appointed a new head for Anonymous Russia named Radis. The new group also announced that it would transform itself into a DDoS-for-hire group that “anyone can purchase.” In the remainder of this document, “Anonymous Russia" refers to the original group led by Raty, not the new group.
RELIGIOUS HACKTIVISM
The politically driven patriotic hacktivists have certainly left on impression since the war in Ukraine started. However, religious hacktivists have been a constant threat across the years and that did not change because of the war. A new group made headlines this year when their attacks aligned with pro-Russian hacktivists. Anonymous Sudan, an allegedly Sudan-based pro-Muslim hacktivist group, was announced as a Killnet cluster member by KillMilk after the group attacked Sweden and Denmark for burning the Quran outside the Turkish embassy in Stockholm by the Danish-Swedish right-wing activist Rusmas Paludan. There is still a lot of controversy and confusion surrounding Anonymous Sudan as a religiously driven activist group. In a report following the DDoS campaigns that targeted Swedish and Danish websites in February 2023, the security firm Truesec concluded that Anonymous Sudan is a false flag operation by the Russian government, leveraged in an information operation to harm and complicate Sweden's NATO application. After targeting Sweden and Denmark, the pro-Islamic group put its crosshairs on French airports, education, health care and government websites motivated by a cartoon of the Prophet Muhammed published by the French magazine Charly Hebdo several years ago. When the pro-Islamic hacktivist crews Team insane pk, Eagle Cyber, and Mysterious Team targeted Australia because an Australian fashion label featured models wearing designs with "Allah walks with me" inscribed in Arabic across the fabric, Anonymous Sudan joined the #OpAustralia campaign and started targeting Australian businesses and government websites with DDoS attacks. At the time of this writing, Anonymous Sudan was able to create a following of over 16k members on its Telegram channel.
Data-driven analysis of global hacktivist DDoS activity
Hacktivists openly publicize their actions on social media and public Telegram channels to gain media attention and raise awareness. They do not operate covertly or evade the media, but instead reveal the names and resources of their targets and attempt to take credit for their attacks. Hacktivists utilize website monitoring tools to demonstrate the impact of their denial-of-service attacks on online resources and frequently share links to reports from online web monitoring tools in their messages. Through tracking and analyzing messages from several active hacktivist groups on Telegram, the Radware Threat Intelligence team assessed the global DDoS activity conducted by hacktivists. In a period spanning two months, from February 18 until April 18, 2023, over 1,800 denial-of-service attacks were claimed by hacktivists across 80 Telegram channels.
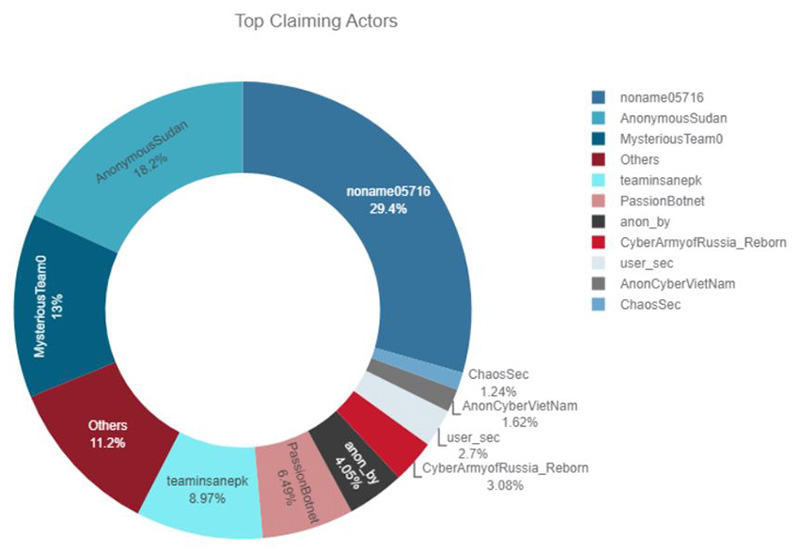 Figure 2: Top Telegram channels claiming successful DDoS attacks
Figure 2: Top Telegram channels claiming successful DDoS attacks
TOP CLAIMING ACTORS
NoName057(16) claimed almost 30% of the attacks, followed by Anonymous Sudan (18%) and Mysterious Team (13%).
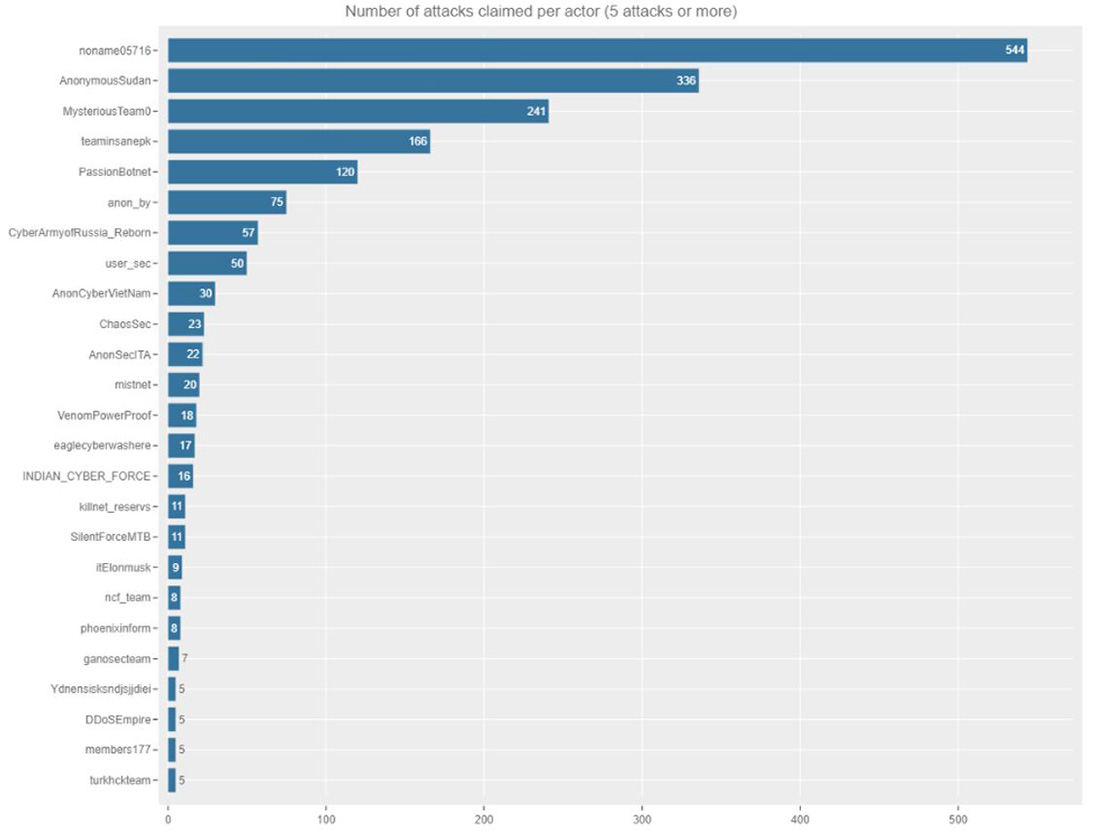 Figure 3: Telegram channels claiming more than five successful DDoS attacks
Figure 3: Telegram channels claiming more than five successful DDoS attacks
Killnet, one of the most notorious groups for its DDoS attack campaigns in 2022, shares the 16th spot on the top ranking and was seen claiming only 11 DDoS attacks in the two months period. This turn of events could be explained by the new activities pursued by its leader, KillMilk. KillMilk announced the formation of a new Private Military Hacker Company (PMHC) called Black Skills. Based on the Russian paramilitary organization, Wagner Private Military Company, Black Skills should become the Wagner of cyber. Black Skills PMHC, according to KillMilk, will be a new structure of hacktivism across the Russian community. An organization with its own laws and goals, with discipline and order. Black Skills PMHC will consist of 24 units, some specializing in intelligence gathering, pentesting, sabotage, psychology operations and other supporting the “business” with HR, accounting, training, investor relations and more.
Hacktivists who share common goals often repost and spread each other's exploits to generate greater attention. However, some groups become overzealous in their pursuit of attention and falsely claim credit for DDoS attacks that were previously claimed by other groups. By monitoring unique report identifiers, it is possible to find the original post of specific report and eliminate duplicate posts from our analysis.
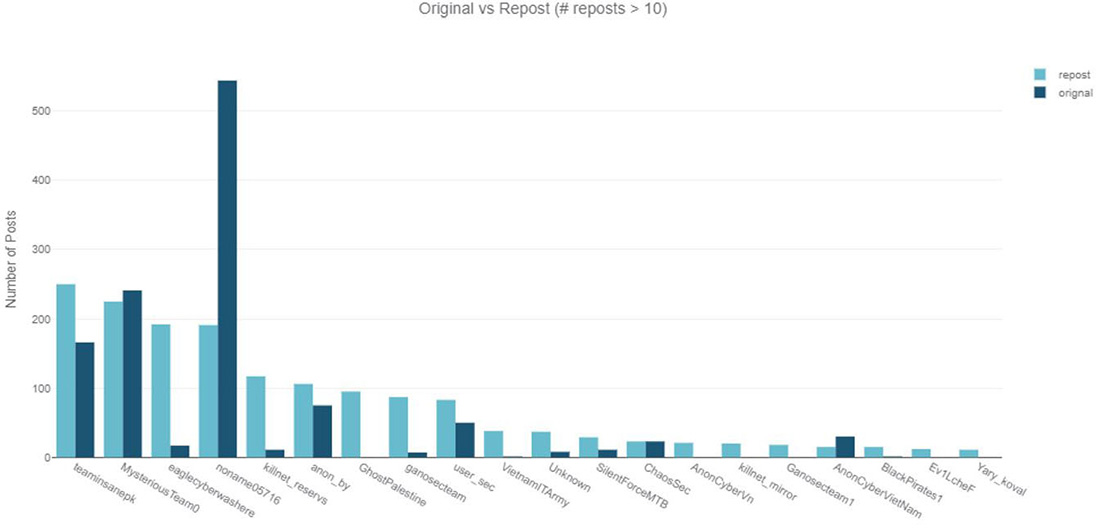 Figure 4: Number of reposts versus original claimed DDoS attacks per Telegram channel
Figure 4: Number of reposts versus original claimed DDoS attacks per Telegram channel
The hacktivist groups Team Insane PK and Mysterious Team, both with pro-Islamic ideologies, have been primarily targeting Australia in their #OpAustralia campaign, as well as India outside of this campaign. It has been observed that these groups frequently repost messages across their channels. However, the most surprising finding from the analysis is that Killnet was found to be reposting ten times more than claiming responsibility for original attacks. The group also did not make it evident that the attacks they posted were performed by members or actors outside of their cluster. Killnet recently has been posting multiple messages containing report links from attacks across several days originally claimed by NoName057(16). Some reports in the messages were several days old when the Killnet channel posted and claimed them.
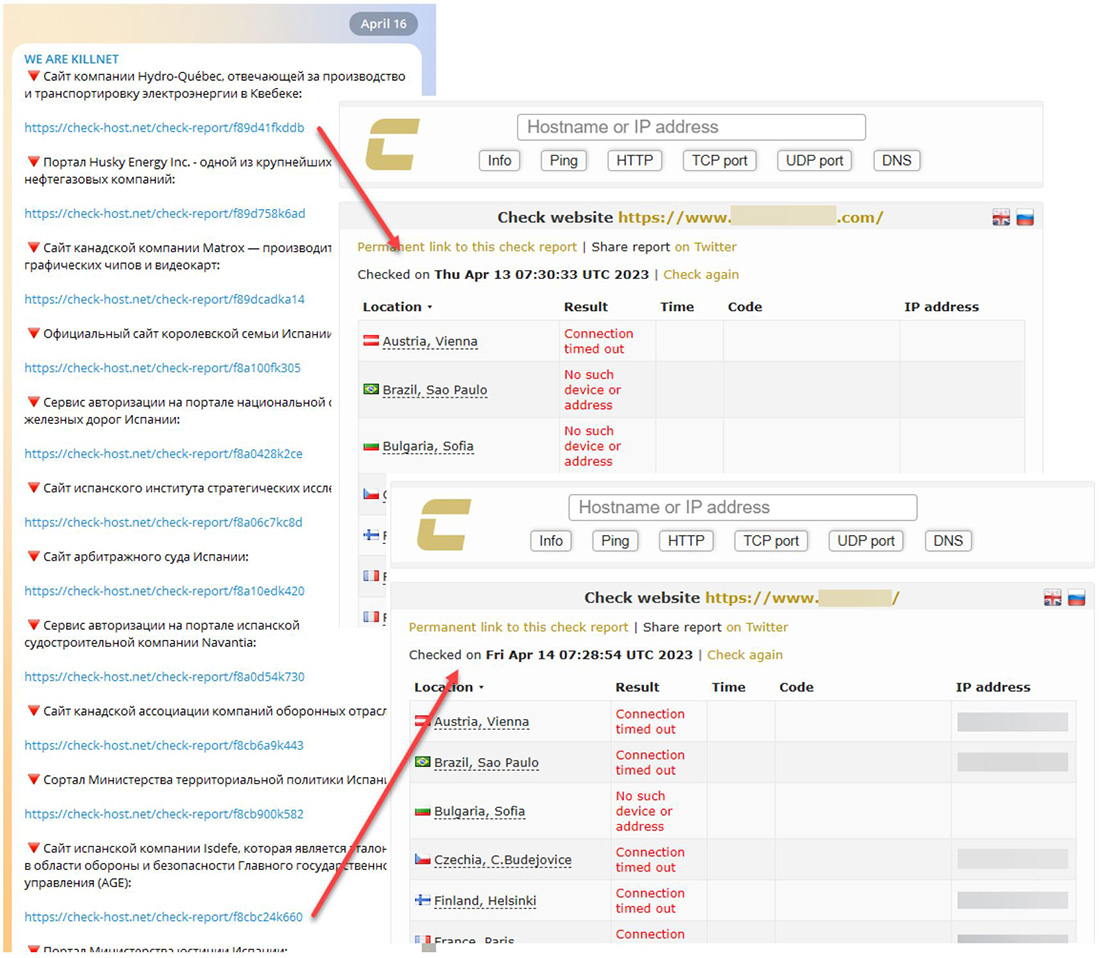 Figure 5: Killnet channel reposting collection of NoName057(16) attack reports from previous days
Figure 5: Killnet channel reposting collection of NoName057(16) attack reports from previous days
TOP TARGETED COUNTRIES
Most of the claimed DDoS attacks were targeting Israel. In the last few weeks, Israel has been a prominent target for pro-Palestinian and pro-Islamic attackers. India has been a constant target for the same pro-Islamic actors that moved focus to Israel and Australia for #OpIsrael and #OpAustralia. Poland is the third most targeted country. Pro-Russian hacktivists have been targeting Poland in relation to the Russo-Ukrainian war on and off for several months now.
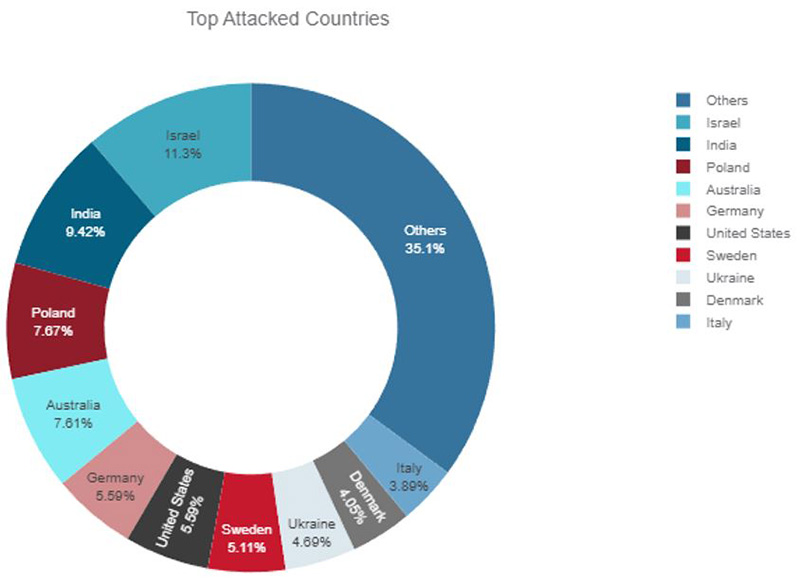 Figure 6: Top attacked countries based on claimed DDoS attacks in Telegram channels
Figure 6: Top attacked countries based on claimed DDoS attacks in Telegram channels
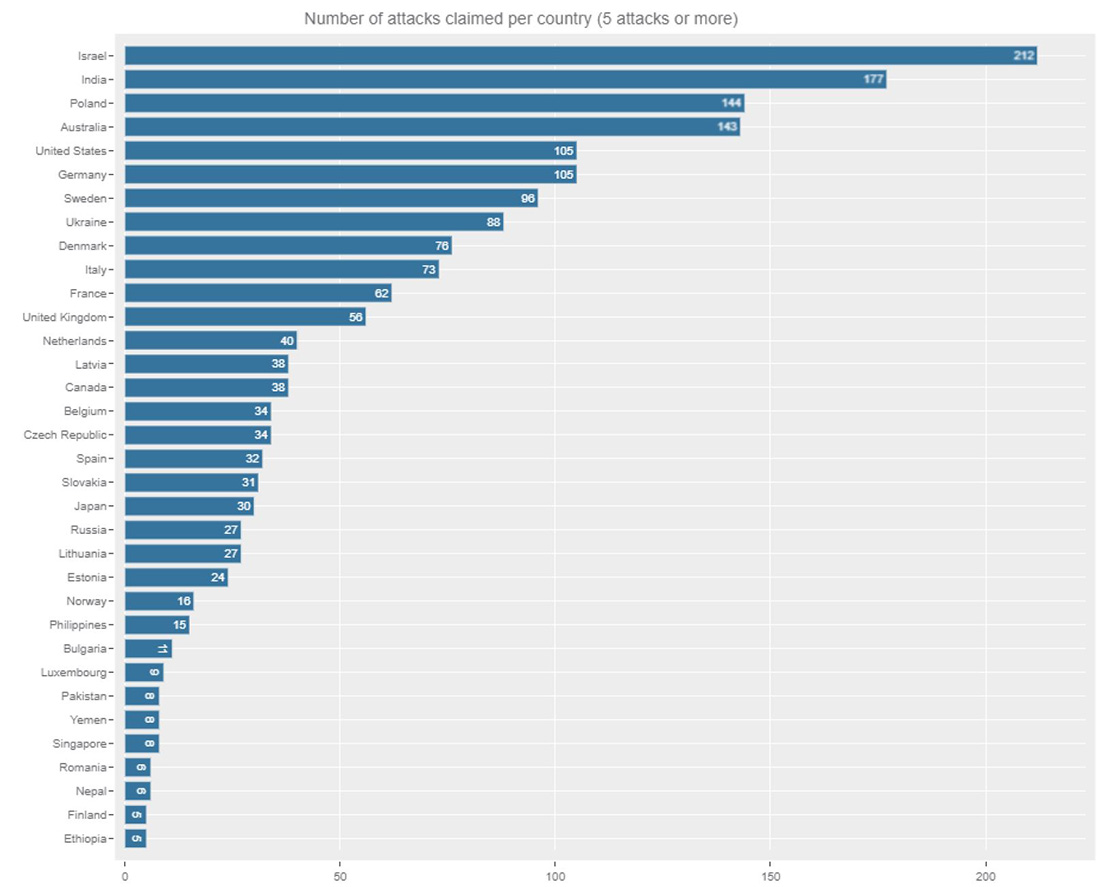 Figure 7: Ranking of attacked countries with at least five claimed attacks on Telegram
Figure 7: Ranking of attacked countries with at least five claimed attacks on Telegram
Attacks by politically driven pro-Russian hacktivists are more widely spread compared to the more focused and operation-based attacks performed by religiously driven hacktivists. Israel, India and Australia were targets of pro-Islamic hacktivists during the recent operations #OpIsrael, #OpIndia and #OpAustralia. Poland, a neighboring country of Ukraine, was targeted almost as much, but over a more extended period than the attacks targeting Australia. United States and Germany, followed by Sweden, Ukraine, Denmark and Italy complete the top 10 of most targeted countries by hacktivists in the last two months.
Figure 7Figure 1 shows the frequency of claimed attacks by country and Telegram Channel. In the two months period of tracking, several pro-Islamic hacktivist groups, including Mysterious Team, Anonymous Sudan, Team Insane PK, Anon Cyber Vietnam, Eagle Cyber, Nigeria Cyber Force, and Ganosec Team, targeted Israel, as well as India and Australia. Meanwhile, Poland was targeted by pro-Russian hacktivist groups NoName057(16) and Anonymous Russia.
From the countries that NoName057(16) targeted, it is evident that the hacktivist is focusing on Western countries that demonstrate support for Ukraine in its conflict with Russia. On the other hand, Mysterious Team, Team Insane PK, and Eagle Cyber were primarily motivated by religion and heavily targeted Australia, Israel and India.
Anonymous Sudan predominantly attacked Sweden, Denmark, Israel, France and Australia and cited religious motivations for every attack campaign against those countries. While there might be doubts about the alignment of Anonymous Sudan to the Russian government, their attack motives and patterns suggest a religiously motivated group rather than a politically motivated one.
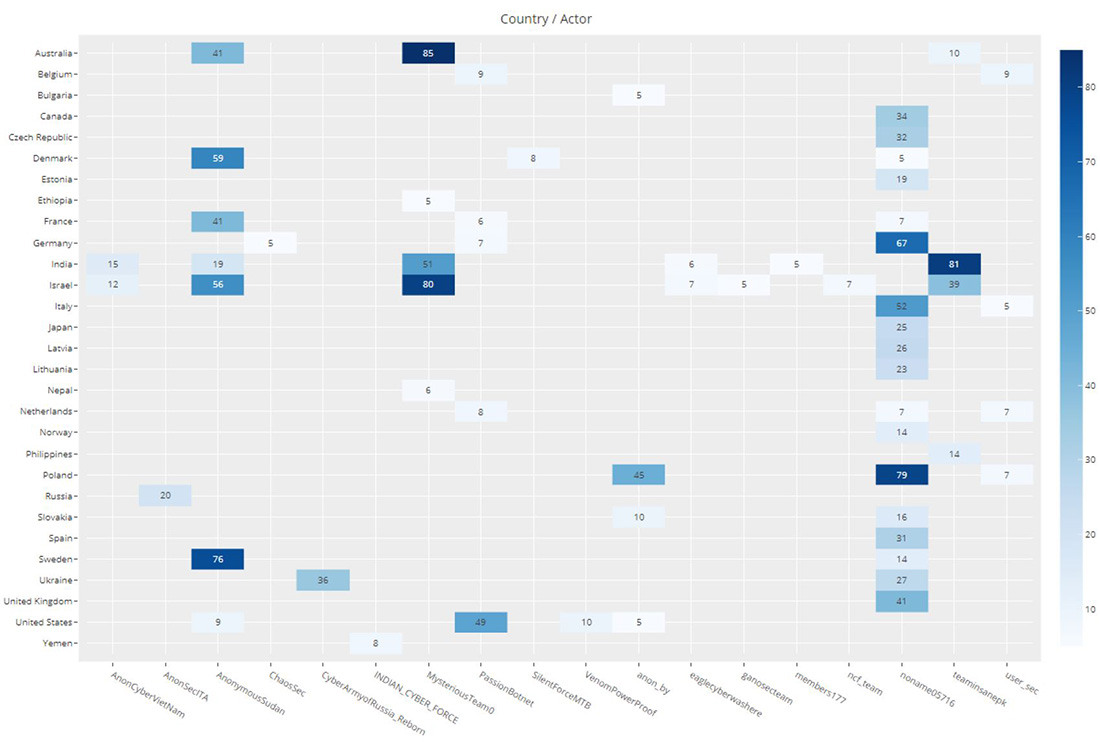 Figure 8: Attacks claimed on Telegram channels by country (attacks claimed > 5)
Figure 8: Attacks claimed on Telegram channels by country (attacks claimed > 5)
TOP TARGETED WEB CATEGORIES
Business/economy, government and travel websites were the most targeted by hacktivists, followed by those focused on financial services, education, health and medicine, and military.
Business/economy websites and government websites were attacked by most of the top hacktivist groups that were tracked during the two-month period. Financial services and travel websites were mostly targeted by NoName057(16), Team Insane PK, Mysterious Team and Anonymous Sudan.
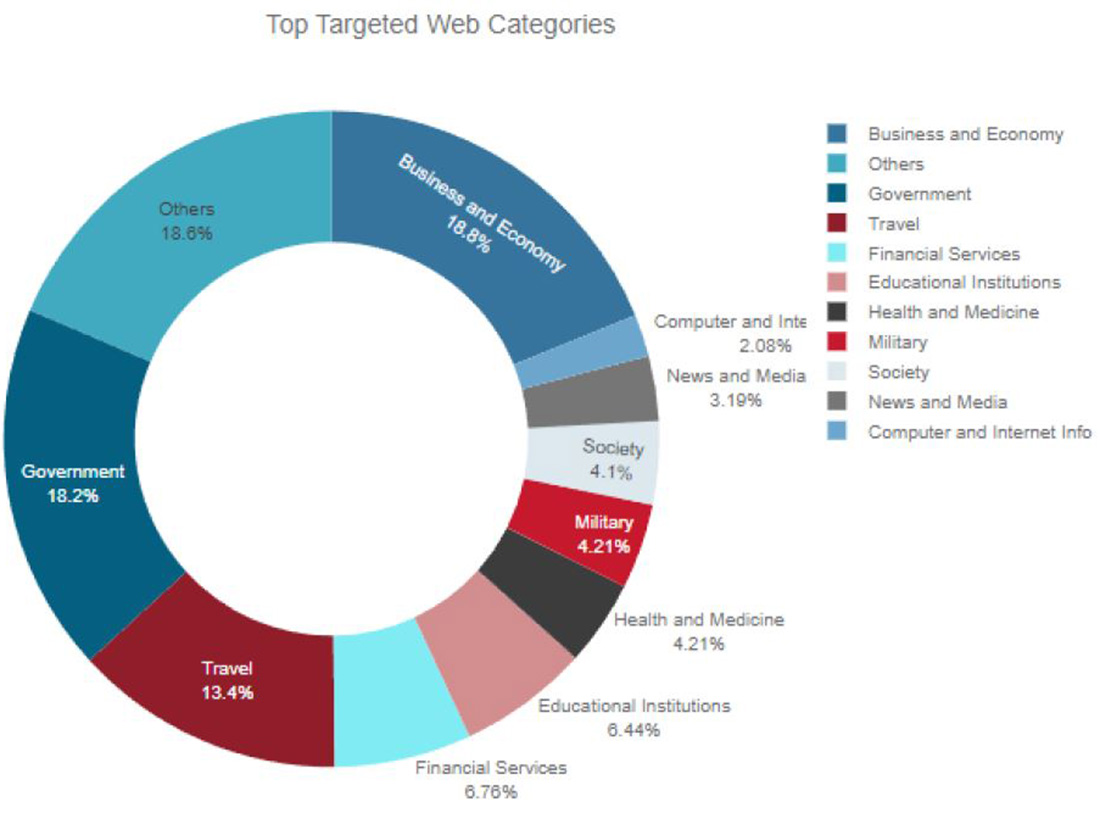 Figure 9: Top website categories targeted by hacktivists globally
Figure 9: Top website categories targeted by hacktivists globally
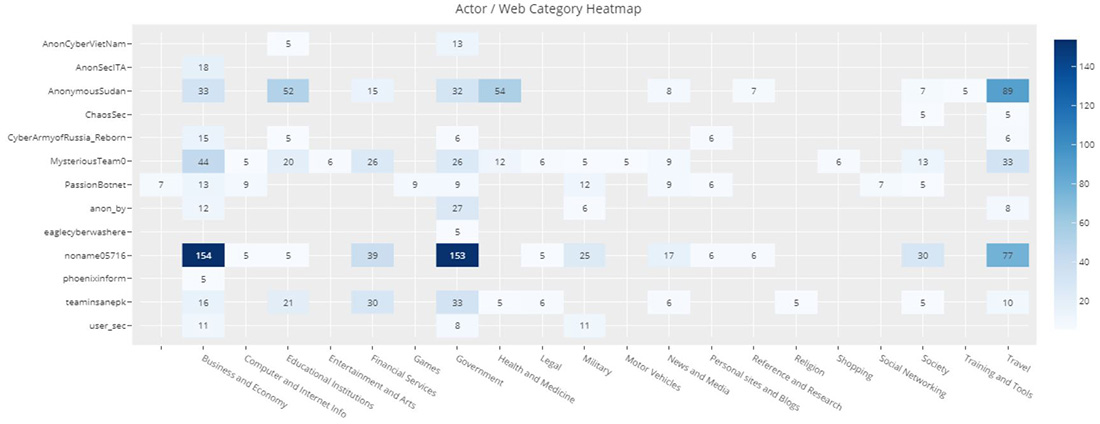 Figure 10: Number of attacks claimed on Telegram channels by website category (attacks claimed > 5)
Figure 10: Number of attacks claimed on Telegram channels by website category (attacks claimed > 5)
Hacktivist Group Analysis
NONAME057(16)
NoName057(16) is a pro-Russian threat group known for launching defacement and DDoS attacks against Ukraine and those that directly or indirectly support Ukraine. The hacktivist group formed in March of 2022 on Telegram and became a notable threat group. While less mediatized compared to Killnet, it is considered one of the most active groups. The group operates in solitary and explicitly noted that they don't want to be associated with their fellow pro-Russian hacktivist group Killnet and its affiliates.
In July 2022, the group quietly launched a crowdsourced botnet project named “DDOSIA.” The project, similar to the pro-Ukrainian Liberator by disBalancer and the fully automated DDoS bot project by the IT ARMY of Ukraine, leverages politically driven hacktivists willing to download and install a bot on their computers to launch denial-of-service attacks. Project DDOSIA, however, raises the stakes by providing financial incentives for the top contributors to successful denial-of-service attacks.
The Ddosia project allows the group to continuously perform DDoS attacks on government and private organization websites, mostly targeting Western nations that support Ukraine during the ongoing invasion of Russia.
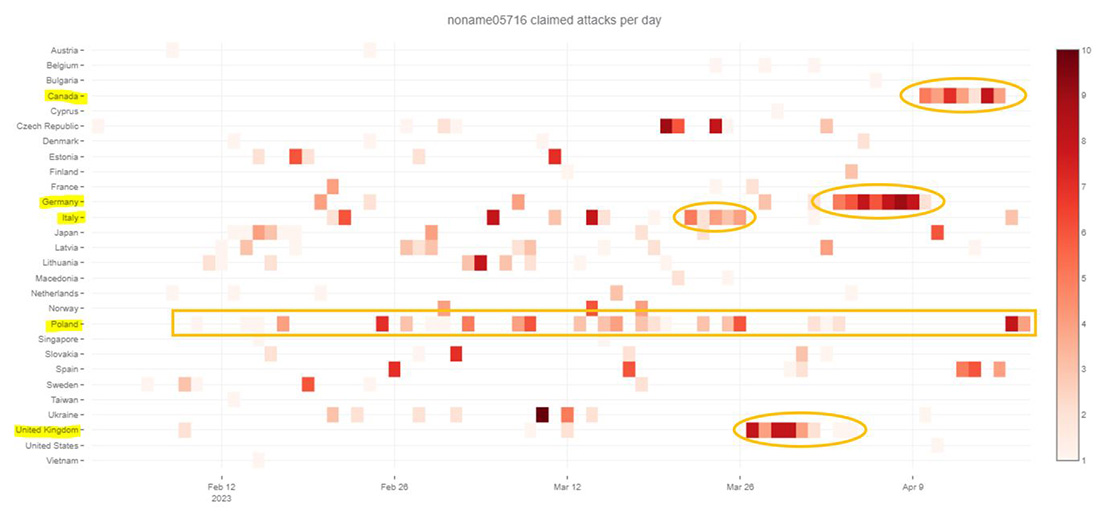 Figure 11: NoName057(16) claimed attacks by country
Figure 11: NoName057(16) claimed attacks by country
Notable attack campaigns by NoName in recent weeks:
- Canada from April 10 to 17
- Germany from April 3 to 10
- United Kingdom from March 27 to April 4
- Italy from March 22 to 26
ANONYMOUS SUDAN
Anonymous Sudan is a group of politically motivated hackers from Sudan who have been conducting denial-of-service attacks against several Swedish and Danish organizations and critical infrastructure under the tags #OpSweden and #OpDenmark, since January 23, 2023. The group claims to be “hacktivists” and their actions are in reaction to a far-right activist, Rasmus Paludan, who holds both Danish and Swedish citizenship, burning the Quran on January 21, 2023, in Sweden and vowing to continue burning the Muslim holy book in Denmark until Sweden is admitted into NATO.
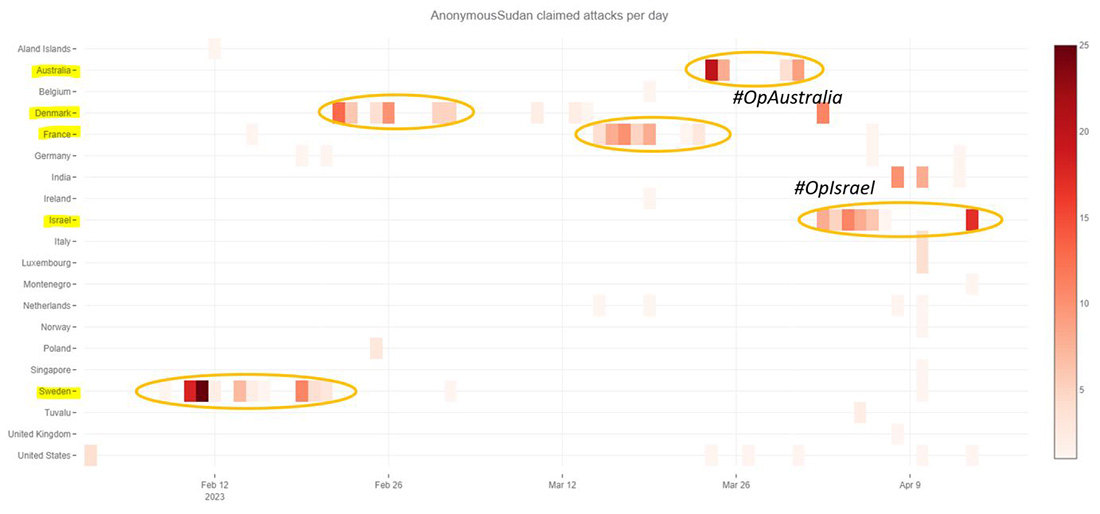 Figure 12: Anonymous Sudan claimed attacks by country
Figure 12: Anonymous Sudan claimed attacks by country
During a multi-day campaign in March 2023, medical facilities, universities and airports in France were targeted by the group. The motivation behind the attacks was a cartoon depiction of the prophet Muhammad, which was allegedly referencing the controversial Charlie Hebdo caricatures.
From France the group moved to Australia to join the pro-Muslim hacktivists Mysterious Team and Team Insane PK in their campaign against Australia under #OpAustralia. By April 2, the pro-Islamic groups moved their crosshairs to Israel to support their pro-Palestinian hacktivists in #OpIsrael and #OpsPetir.
MYSTERIOUS TEAM BANGLADESH & TEAM INSANE PK
The hacktivist groups Mysterious Team Bangladesh and Team Insane PK have relations with the other Indonesian hacktivist groups such as Ganosec Team. Many of their tools and techniques are similar to the notorious pro-Palestinian hacktivist group DragonForce Malaysia. These groups have been targeting Indian government websites throughout 2022 and continued their assaults in 2023 with continuous activity in India.
Mysterious Team was the group that initiated #OpAustralia and joined the other pro-Muslim groups during #OpIsrael and #OpsPetir.
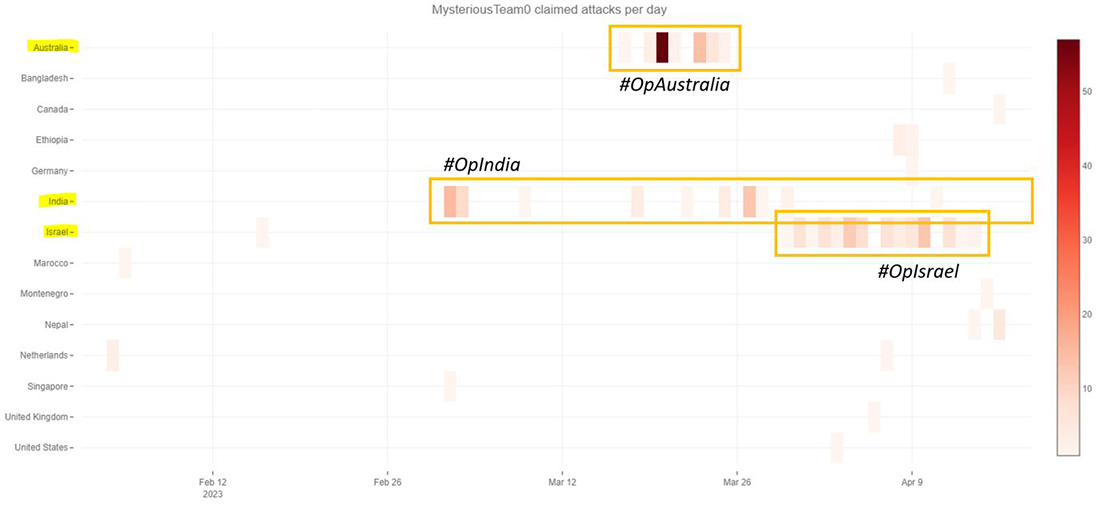 Figure 13: Mysterious Team claimed attacks by country
Figure 13: Mysterious Team claimed attacks by country
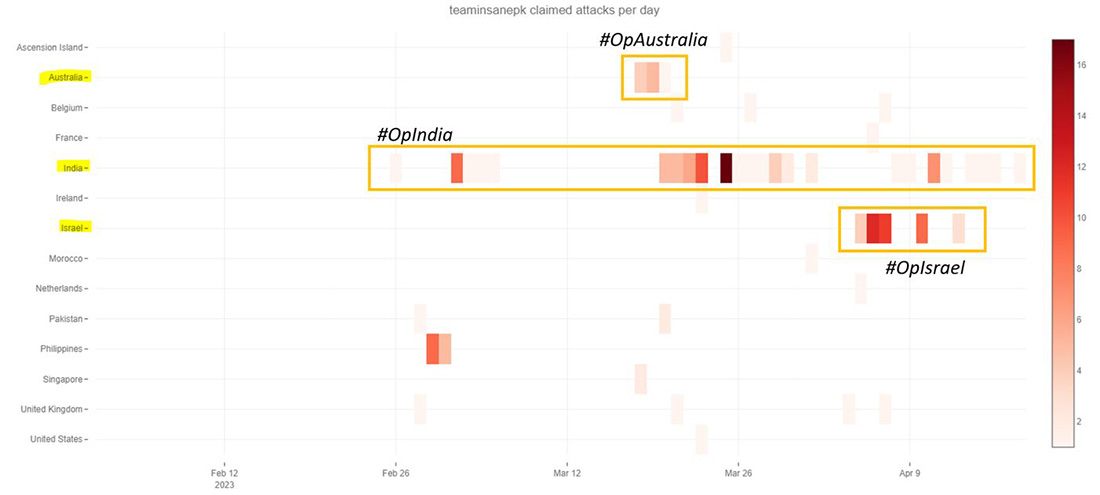 Figure 14: Team Insane PK claimed attacks by country
Figure 14: Team Insane PK claimed attacks by country
Country Level Analysis
ISRAEL
In recent weeks, Israel was the target by pro-Islamic hacktivists targeting the country with denial-of-service attacks, website defacements and attempts at stealing and leaking sensitive information. Mysterious Team, Anonymous Sudan and Team Insane PK were the most active groups, targeting mostly travel, education and government institutions with DDoS attacks.
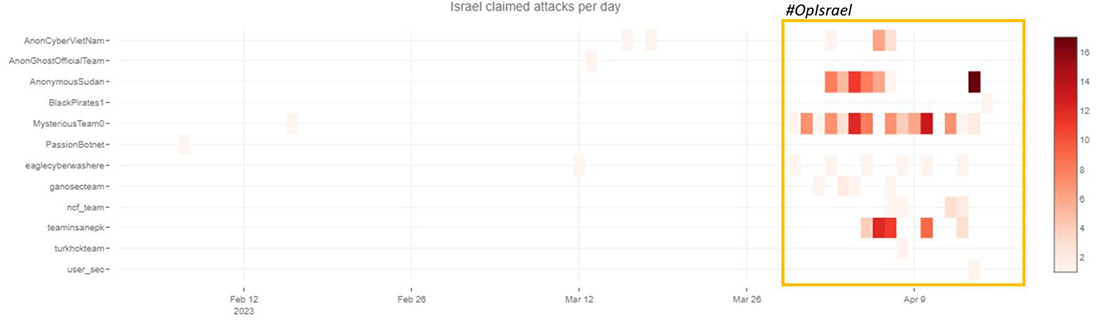 Figure 15: Claimed attacks by Telegram channel targeting Israel
Figure 15: Claimed attacks by Telegram channel targeting Israel
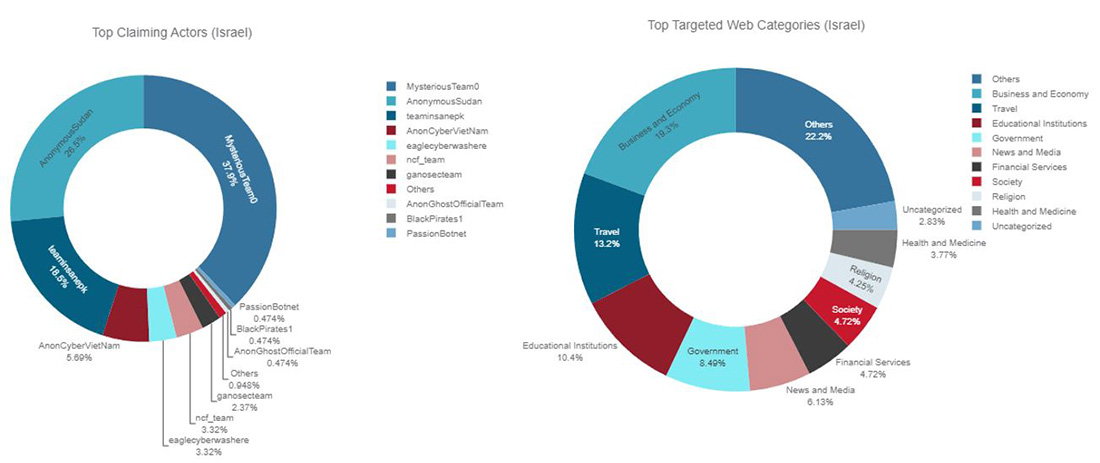 Figure 16: Top claiming Telegram channels and top targeted website categories for Israel
Figure 16: Top claiming Telegram channels and top targeted website categories for Israel
AUSTRALIA
On Saturday March 11, during the final show of the Melbourne Fashion Festival, a model of the Australian luxury streetwear label "Not a Main's Dream" walked down the catwalk wrapped in a transparent fabric with the Arabic inscription "Allah walks with me" across her body. In response, the Muslim hacktivist community aligned forces and started attacking Australian infrastructure and private organizations under the operation tags #OpAustralia and #opsjentik. By Friday, March 17, Not A Man's Dream was the prominent target for Muslim hacktivists. The following weeks, over one hundred Australian websites—including the public websites of governments, ports, banks, and private businesses—were the target of denial-of-service attacks.
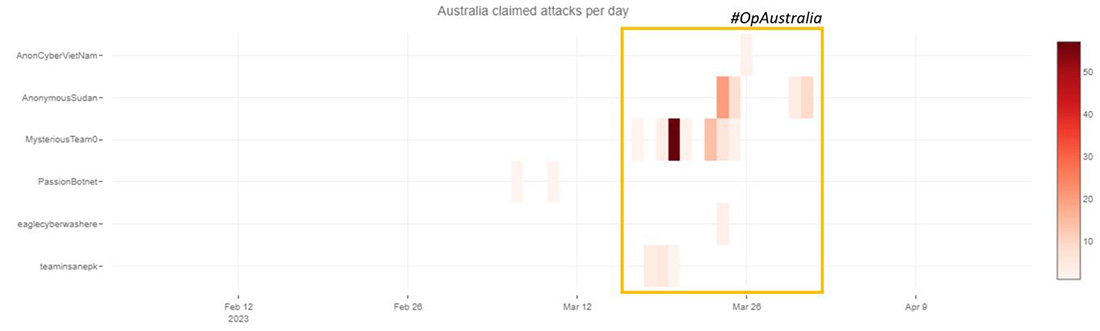 Figure 17: Claimed attacks by Telegram channel targeting Australia
Figure 17: Claimed attacks by Telegram channel targeting Australia
Mysterious Team and Anonymous Sudan were the most active, followed by Team Insane PK. The most targeted website categories were travel, business and economy, education, health care and government.
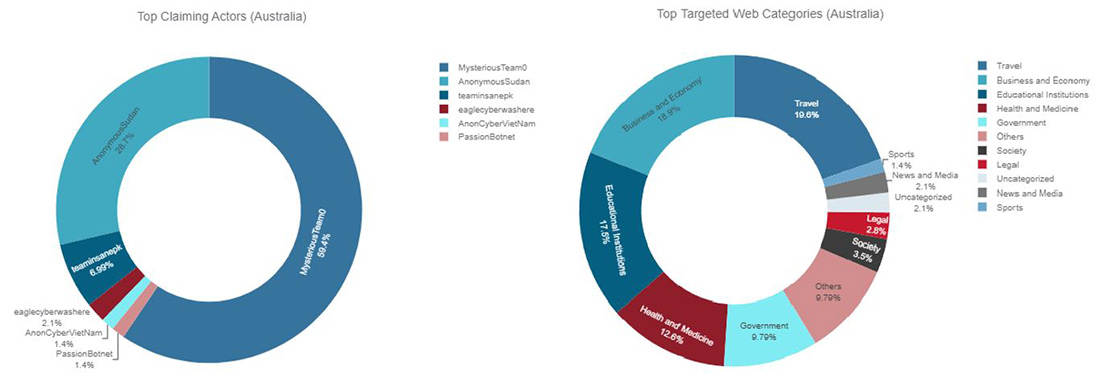 Figure 18: Top claiming Telegram channels and top targeted website categories for Australia
Figure 18: Top claiming Telegram channels and top targeted website categories for Australia
POLAND
At the end of December 2022, the Polish Special Services published a report on Russian cyberattacks. Since the outbreak of war in Ukraine, Poland has been one of the critical targets of cybercriminals and has seen its number of incidents growing exponentially. Some of these hostile campaigns can be linked directly to the activities of pro-Russian hacking groups. The assertion of the DDoS hacktivist on Telegram substantiates this statement and exhibits the persistence of this pattern in 2023. Poland ranks number three on the global list of claimed hacktivist DDoS activity, behind Israel and India, just in front of Australia. Israel, India and Australia are targets of religious hacktivists, while Poland is the only country in the top five that is specifically targeted by pro-Russian hacktivists in attacks relating to the Russo-Ukrainian war.
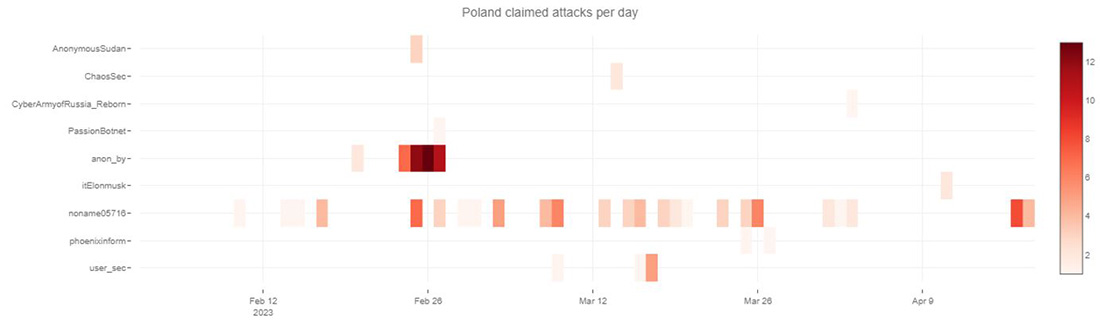 Figure 19: Claimed attacks by Telegram channel targeting Poland
Figure 19: Claimed attacks by Telegram channel targeting Poland
NoName057(16) claimed responsibility for more than half of the DDoS attacks targeting Polish websites. Anonymous Russia claimed more than 30% of the attacks. The attacks targeted mostly government websites, followed by business and economy, travel and financial services.
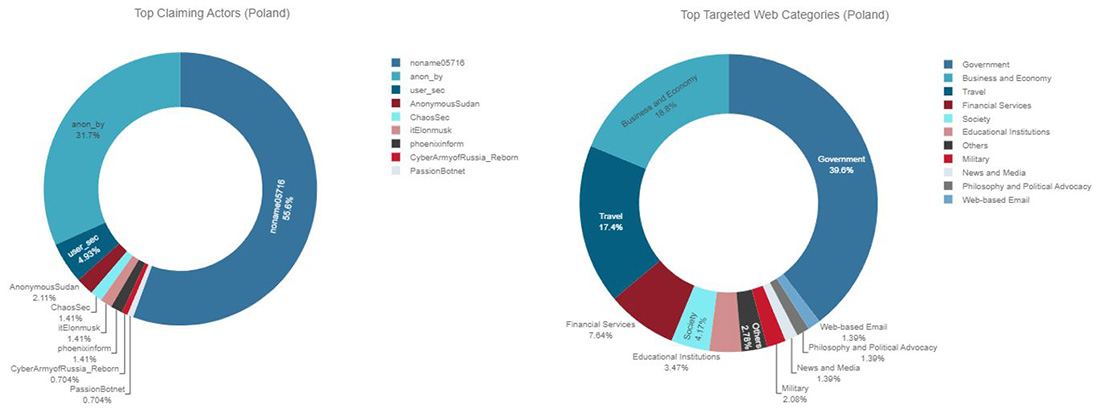 Figure 20: Top claiming Telegram channels and top targeted website categories for Poland
Figure 20: Top claiming Telegram channels and top targeted website categories for Poland
UKRAINE
Ukraine takes the eighth spot on the global hacktivist target ranking, behind similar, politically targeted, Western nations Poland, United States, Germany and Sweden.
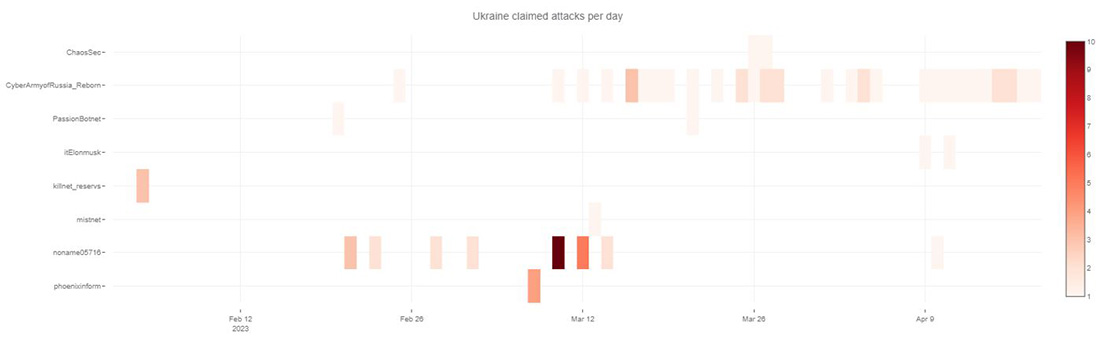 Figure 21: Claimed attacks by Telegram channel targeting Ukraine
Figure 21: Claimed attacks by Telegram channel targeting Ukraine
The most active group claiming DDoS attacks against Ukraine was the Cyber Army of Russia, followed by NoName057(16).
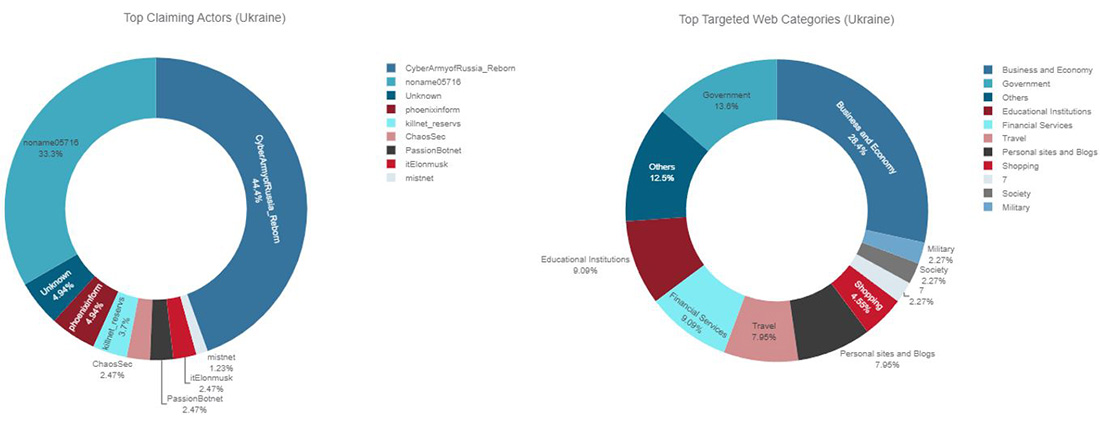 Figure 22: Top claiming Telegram channels and top targeted website categories for Ukraine
Figure 22: Top claiming Telegram channels and top targeted website categories for Ukraine
The Cyber Army of Russia has only been sporadically targeting other countries outside of Ukraine. The hacktivist is focused on Ukraine, unlike NoName057(16) who casts a much wider net across the globe and moves its crosshairs to whatever country made the press with events relating to the Russo-Ukrainian war.
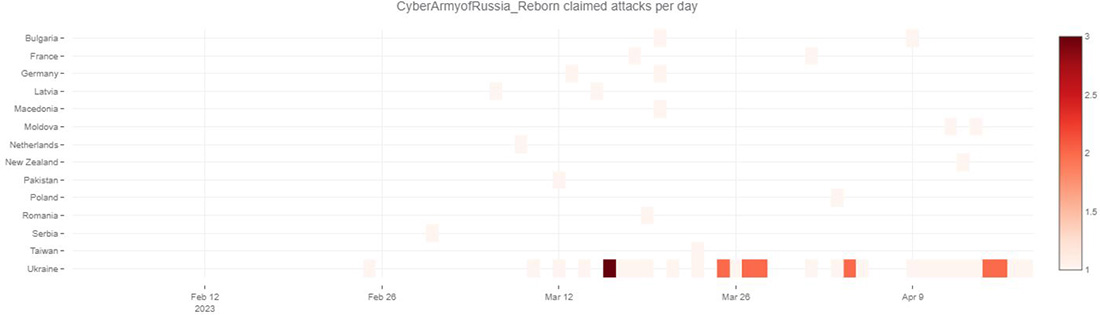 Figure 23: Claimed DDoS attacks on the Telegram channel of Cyber Army of Russia
Figure 23: Claimed DDoS attacks on the Telegram channel of Cyber Army of Russia
INDIA
India has been plagued by multiple waves of attacks targeting Indian government and private entities with DDoS and defacement attacks in 2022. Pro-Islamic hacktivist groups Team Insane PK and Mysterious Team Bangladesh have led the charge here. Recently, Anonymous Sudan joined the ranks and started to target more often Indian websites with DDoS attacks.
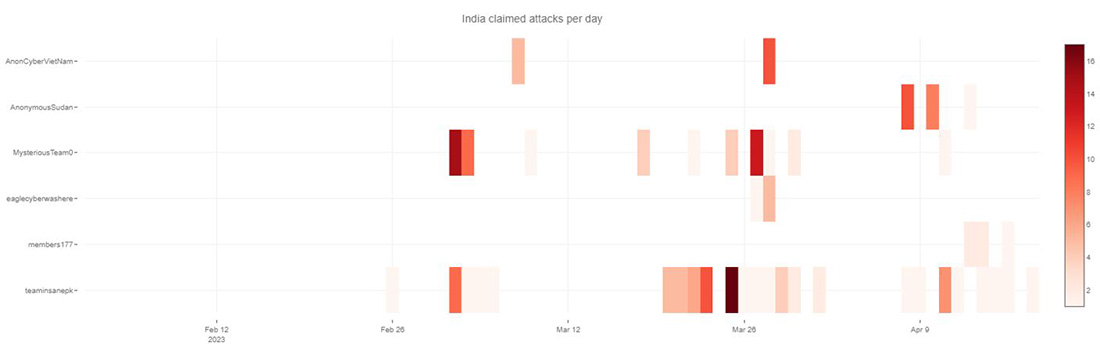 Figure 24: Claimed attacks by Telegram channel targeting India
Figure 24: Claimed attacks by Telegram channel targeting India
Financial services and government, representing over 50% of the total hacktivist DDoS activity, are the most targeted categories of websites in India, followed by education and health care.
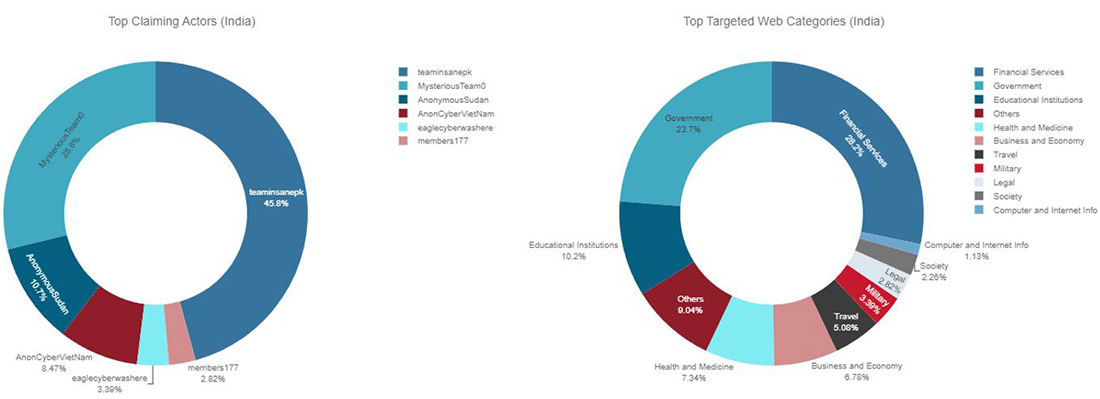 Figure 25: Top claiming Telegram channels and top targeted website categories for India
Figure 25: Top claiming Telegram channels and top targeted website categories for India
UNITED STATES
In a large assortment of actors, one specific group, Passion, stood out across the two months of activity targeting US websites. The origins of the Passion group remain unknown, but they have made their presence known since the start of 2023. The group, affiliated with Killnet and Anonymous Russia, has been associated with defacement and denial-of-service attacks targeting individuals and organizations who do not support the Russian invasion of Ukraine. Passion has a strong online presence through its Telegram channels, some dating back to March 2022. Other hacktivist groups, such as Anonymous Russia, MIRAI, Venom, and Killnet, have promoted Passion.
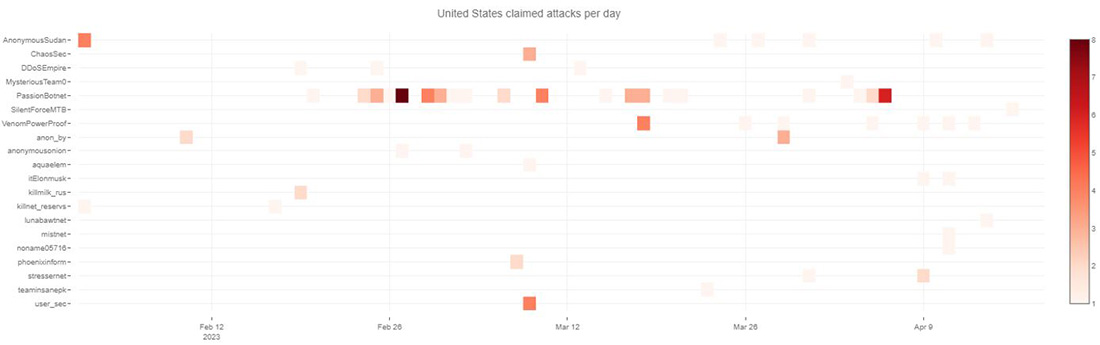 Figure 26: Claimed attacks by Telegram channel targeting United States
Figure 26: Claimed attacks by Telegram channel targeting United States
Since its inception, Passion group's tactics, techniques, and procedures resembled those of the other hacktivist groups involved in the Russo-Ukrainian conflict. In 2023, however, Passion group began offering DDoS-as-a-Service to pro-Russian hacktivists. The Passion Botnet was leveraged during the attacks on January 27, targeting medical institutions in the USA, Portugal, Spain, Germany, Poland, Finland, Norway, Netherlands and the United Kingdom as retaliation for sending tanks in support of Ukraine. Since 2023, the group's motivations and their choice of targets for DDoS attacks is primarily driven by an economic objective. Passion Group likes to target high-profile organizations to demonstrate their botnet's capabilities and promote their DDoS-for-hire services within the pro-Russian hacktivist community. Passion has been targeting a slew of large, US-based cloud organizations including Facebook, Uber, Nasa, Reddit, WSJ, Amazon and Google. The group does, on occasion, align their attacks with the campaigns of other pro-Russian hacktivists, but that is believed to be mainly in support of their economic objectives and, in lesser part, to support the political narrative of the pro-Russian hacktivists' campaigns.
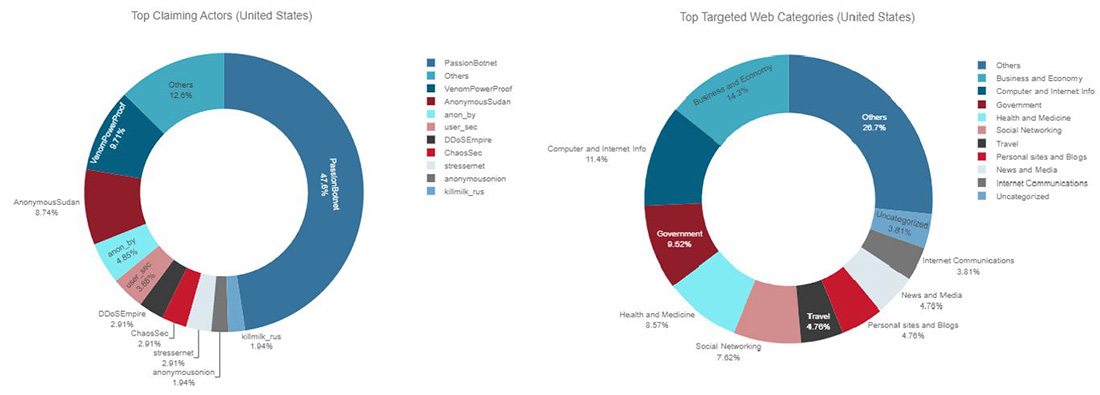 Figure 27: Top claiming Telegram channels and top targeted website categories for United States
Figure 27: Top claiming Telegram channels and top targeted website categories for United States
Concluding
Muslim hacktivists have shown to be well connected and have a large circle of influence. Many of the tracked hacktivist groups are running multiple concurrent operations, amongst which #OpIndia is a recurring topic. The attacks are motivated by religion, a very common motivation for hacktivists.
In other parts of the world, Pro-Russian hacktivists have been actively attacking anyone who supports Ukraine or goes against Russia for over a year now. Killnet has been dedicated to its cause and has had the time to build experience and increase its circle of influence across affiliate pro-Russian hacktivist groups. We’ve seen groups like NoName057(16) successfully exploring crowd-sourced botnets with financial incentives and Passion group providing DDoS-as-a-service attacks to like-minded groups. While NoName057(16) is the major force to be reckoned with in terms of DDoS attacks, Killnet’s influence, reach and tactics are growing and changing, and they are not showing signs of slowing down or retiring soon.
Hacktivists' main objective is getting noticed and spreading their message, either through defacing public websites or making them unavailable through denial-of-service attacks. DDoS attacks are not the hardest to pull off. The hacktivist movements created after the invasion of Ukraine by Russia democratized DDoS attacks and made them more accessible while improving existing tools to make the attacks more sophisticated and more powerful. There’s also a sizable number of supporting services such as free and paying anonymous proxy providers and providers of pay and go DDoS-for-hire services like Clearnet booter and stresser services.
Denial of service has always been an important tactic for hacktivist groups, and this will not change any time soon. Any organization, independent of size and vertical, can become a target of hacktivists. There is no reason for panic, but organizations need to be prepared. It is widely known in the security community that disrupting or impacting an organization or infrastructure requires more perseverance than skills or sophistication.
EFFECTIVE DDOS PROTECTION ESSENTIALS
Hybrid DDoS Protection – Use on-premise and cloud DDoS protection for real-time DDoS attack prevention that also addresses high-volume attacks and protects from pipe saturation
Behavioral-Based Detection - Quickly and accurately identify and block anomalies while allowing legitimate traffic through
Real-Time Signature Creation - Promptly protect against unknown threats and zero-day attacks
A Cyber-Security Emergency Response Plan - A dedicated emergency team of experts who have experience with Internet of Things security and handling IoT outbreaks
Intelligence on Active Threat Actors – High fidelity, correlated and analyzed data for preemptive protection against currently active known attackers
For further network and application protection measures, Radware urges companies to inspect and patch their network to defend against risks and threats.
EFFECTIVE WEB APPLICATION SECURITY ESSENTIALS
- Full OWASP Top-10 coverage against defacements, injections, etc.
- Low false positive rate using negative and positive security models for maximum accuracy
- Auto-policy generation capabilities for the widest coverage with the lowest operational effort
- Bot protection and device fingerprinting capabilities to overcome dynamic IP attacks and achieve improved bot detection and blocking
- Securing APIs by filtering paths, understanding XML and JSON schemas for enforcement, and using activity tracking mechanisms to trace bots and guard internal resources
- Flexible deployment options - on-premises, out-of-path, virtual or cloud-based
LEARN MORE AT RADWARE’S SECURITY RESEARCH CENTER
To know more about today’s attack vector landscape, understand the business impact of cyberattacks, or learn more about emerging attack types and tools, visit Radware’s Security Research Center. Additionally, visit Radware’s Quarterly DDoS & Application Threat Analysis Center for quarter-over-quarter analysis of DDoS and application attack activity based on data from Radware’s cloud security services and threat intelligence.